Inhaltsverzeichnis
Stellar Wireless DSPSK via OmniVista UPAM Radius Proxy zu externem Radius Server
In diesem Artikel wird beschrieben wie Stellar Wireless gerätespezifische Pre-Shared-Keys (Stellar DSPSKs) von einem externen Radius Server verwenden kann. Dabei verwendet der Nutzer einen ihm/dem Gerät zugewiesenen PSK und dieser wird auch in dieser Form im externen Radius hinterlegt (in diesem Fall ist dies kein Eintrag in „OmniVista: Company Property“).
In OmniVista v4.5R2 kann die Funktion wie hier beschrieben nur dann verwendet werden, wenn Authenticated Switch Access in UPAM nicht verwendet wird.
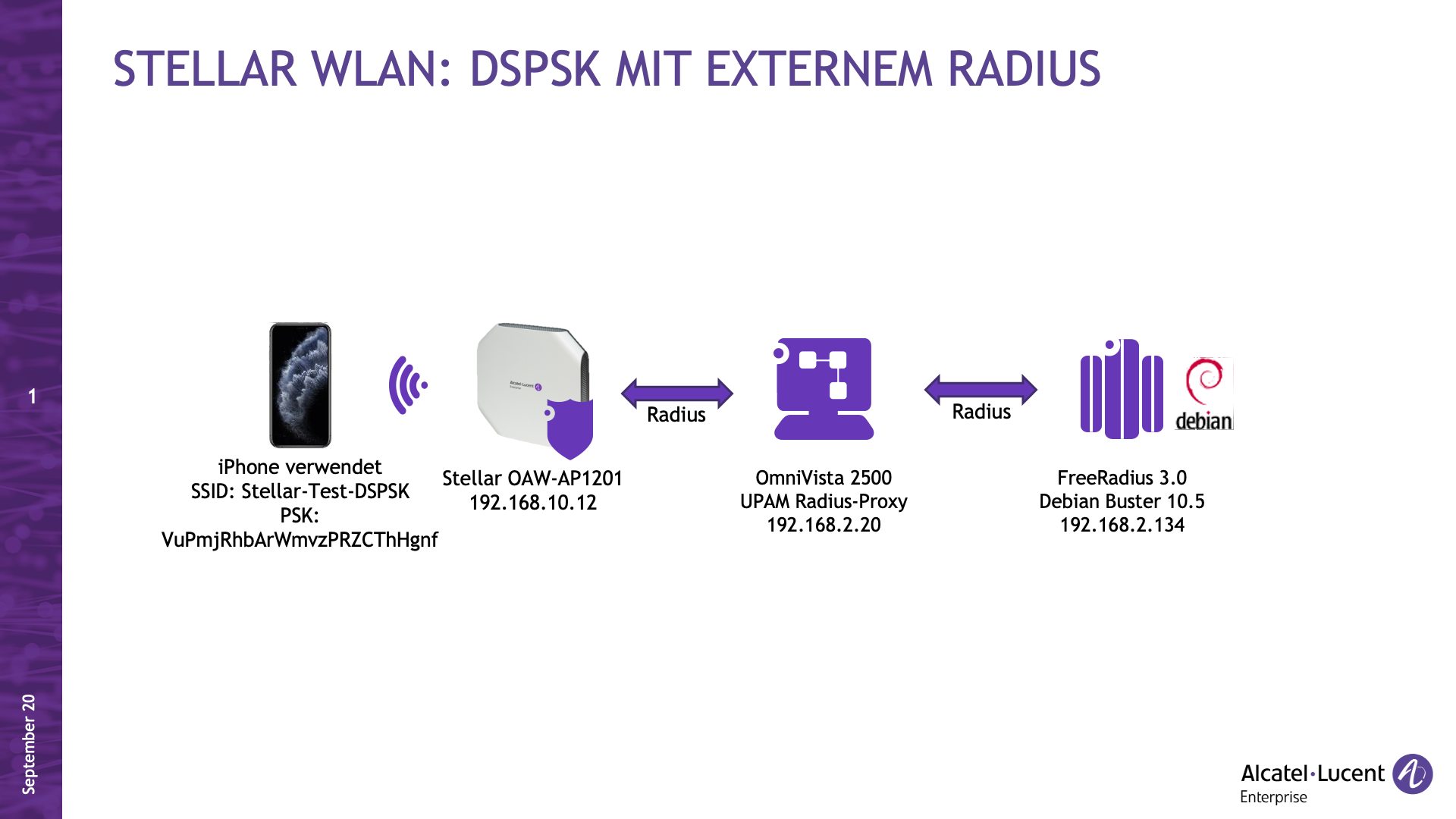
Aufbau / Zeichnung
Konfiguration des externen Radius Servers (freeradius 3.0)
Wir beginnen mit der Konfiguration des externen Radius Servers, in diesem Fall ein freeradius 3.0 auf Debian Buster 10.5.
freeradius 3.0 - clients.conf
Entsprechend die Freigabe für die Abfrage Stellar AP → OmniVista UPAM Proxy → Externer Radius Server einrichten.
sudo vi /etc/freeradius/3.0/clients.conf
# IP Subnetz/Host von OmniVista 2500 UPAM
client stellar-ext-radius {
ipaddr = 192.168.2.0/24
secret = ext-radius-2020
}
freeradius 3.0 - dictionary.xylan
Damit wir das „ALE-Stellar-DSPSK“-Attribut verwenden können, müssen wir dieses dem freeradius bekanntmachen. Je nach Distribution kann der Pfad abweichen.
sudo vi /usr/share/freeradius/dictionary.xylan # Eintrag nach Xylan-Acce-Priv-F-W2 einfuegen: ATTRIBUTE ALE-Stellar-DSPSK 155 string
freeradius 3.0 - users
Wenn es sich um eine neue freeradius Installation handelt, können je nach Distribution und mitgelieferter Konfiguration noch ein paar DEFAULT-Einträge in der users-Datei sein. Diese sollte man natürlich im Hinterkopf haben, damit der Access-Request auch bis zum Benutzer (MAC-ADDR) ankommt.
sudo vi /etc/freeradius/3.0/users
# Je nachdem was fuer ein Format gewaehlt wurde oder
# via OmniVista -> WLAN -> SSIDs -> (DSPSK-SSID) -> Advanced AAA Configuration
# festgelegt wurde.
# Im externen Radius ist der PSK im Cleartext-Format hinterlegt.
# Das PSK fuer das Endgeraet f0:c3:71:2e:fd:8d ist also "VuPmjRhbArWmvzPRZCThHgnf".
# Mit der Filter-Id koennte man das UNP der SSID uebersteuern um z.B. Mbps Limits festzulegen
# Achtung: Diese UNPs muessen natuerlich vorher auf die AP-Gruppe ausgerollt werden!
#
# Typisch waeren standardmaeszig GROSSSCHREIBUNG und keine Trennzeichen
#F0C3712EFD8D Cleartext-Password := "F0C3712EFD8D"
# Mein Beispiel verwendet aber ein anderes Format:
f0:c3:71:2e:fd:8d Cleartext-Password := "f0c3712efd8d"
# Cleartext: VuPmjRhbArWmvzPRZCThHgnf
ALE-Stellar-DSPSK = "VuPmjRhbArWmvzPRZCThHgnf"
#Filter-Id = "dspsk1mbps"
freeradius 3.0 - Debug-Log-Ausgabe
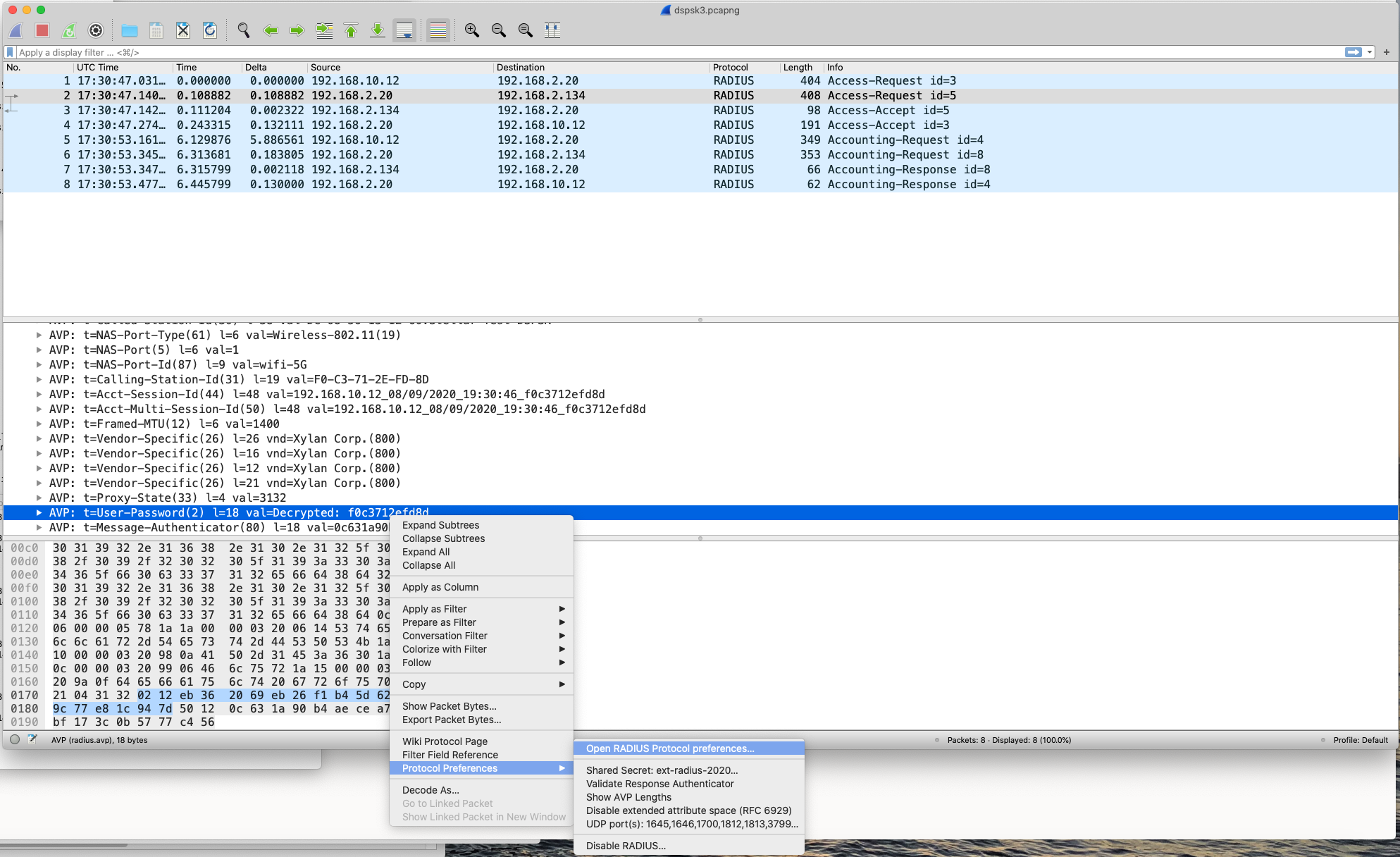
Passend dazu auch das Wireshark PCAPNG: dspsk3.pcapng.zip Radius Shared Secret zwischen OmniVista UPAM und dem externen freeradius 3.0 ist ext-radius-2020
sudo freeradius -X
...
Ready to process requests
(0) Received Access-Request Id 5 from 192.168.2.20:1814 to 192.168.2.134:1812 length 366
(0) User-Name = "f0:c3:71:2e:fd:8d"
(0) Service-Type = Call-Check
(0) NAS-IP-Address = 192.168.10.12
(0) NAS-Identifier = "Stellar-Test-DSPSK"
(0) Called-Station-Id = "DC-08-56-13-1E-60:Stellar-Test-DSPSK"
(0) NAS-Port-Type = Wireless-802.11
(0) NAS-Port = 1
(0) NAS-Port-Id = "wifi-5G"
(0) Calling-Station-Id = "F0-C3-71-2E-FD-8D"
(0) Acct-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(0) Acct-Multi-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(0) Framed-MTU = 1400
(0) Xylan-Port-Desc = "Stellar-Test-DSPSK"
(0) Attr-26.800.152 = 0x41502d31453a3630
(0) Attr-26.800.153 = 0x466c7572
(0) Attr-26.800.154 = 0x64656661756c742067726f7570
(0) Proxy-State = 0x3132
(0) User-Password = "f0c3712efd8d"
(0) Message-Authenticator = 0x0c631a90b4aecea7bf173c0b5777c456
(0) # Executing section authorize from file /etc/freeradius/3.0/sites-enabled/default
(0) authorize {
(0) policy filter_username {
(0) if (&User-Name) {
(0) if (&User-Name) -> TRUE
(0) if (&User-Name) {
(0) if (&User-Name =~ / /) {
(0) if (&User-Name =~ / /) -> FALSE
(0) if (&User-Name =~ /@[^@]*@/ ) {
(0) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(0) if (&User-Name =~ /\.\./ ) {
(0) if (&User-Name =~ /\.\./ ) -> FALSE
(0) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(0) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(0) if (&User-Name =~ /\.$/) {
(0) if (&User-Name =~ /\.$/) -> FALSE
(0) if (&User-Name =~ /@\./) {
(0) if (&User-Name =~ /@\./) -> FALSE
(0) } # if (&User-Name) = notfound
(0) } # policy filter_username = notfound
(0) [preprocess] = ok
(0) [chap] = noop
(0) [mschap] = noop
(0) [digest] = noop
(0) suffix: Checking for suffix after "@"
(0) suffix: No '@' in User-Name = "f0:c3:71:2e:fd:8d", looking up realm NULL
(0) suffix: No such realm "NULL"
(0) [suffix] = noop
(0) eap: No EAP-Message, not doing EAP
(0) [eap] = noop
(0) files: users: Matched entry f0:c3:71:2e:fd:8d at line 104
(0) [files] = ok
(0) [expiration] = noop
(0) [logintime] = noop
(0) [pap] = updated
(0) } # authorize = updated
(0) Found Auth-Type = PAP
(0) # Executing group from file /etc/freeradius/3.0/sites-enabled/default
(0) Auth-Type PAP {
(0) pap: Login attempt with password
(0) pap: Comparing with "known good" Cleartext-Password
(0) pap: User authenticated successfully
(0) [pap] = ok
(0) } # Auth-Type PAP = ok
(0) # Executing section post-auth from file /etc/freeradius/3.0/sites-enabled/default
(0) post-auth {
(0) update {
(0) No attributes updated
(0) } # update = noop
(0) [exec] = noop
(0) policy remove_reply_message_if_eap {
(0) if (&reply:EAP-Message && &reply:Reply-Message) {
(0) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE
(0) else {
(0) [noop] = noop
(0) } # else = noop
(0) } # policy remove_reply_message_if_eap = noop
(0) } # post-auth = noop
(0) Sent Access-Accept Id 5 from 192.168.2.134:1812 to 192.168.2.20:1814 length 0
(0) ALE-Stellar-DSPSK = "VuPmjRhbArWmvzPRZCThHgnf"
(0) Proxy-State = 0x3132
(0) Finished request
Waking up in 4.9 seconds.
(0) Cleaning up request packet ID 5 with timestamp +21
Ready to process requests
(1) Received Accounting-Request Id 8 from 192.168.2.20:1815 to 192.168.2.134:1813 length 311
(1) Acct-Status-Type = Start
(1) Acct-Authentic = RADIUS
(1) User-Name = "f0:c3:71:2e:fd:8d"
(1) NAS-IP-Address = 192.168.10.12
(1) NAS-Identifier = "Stellar-Test-DSPSK"
(1) Called-Station-Id = "DC-08-56-13-1E-60:Stellar-Test-DSPSK"
(1) NAS-Port-Type = Wireless-802.11
(1) NAS-Port = 1
(1) NAS-Port-Id = "wifi-5G"
(1) Calling-Station-Id = "F0-C3-71-2E-FD-8D"
(1) Acct-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(1) Acct-Multi-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(1) Filter-Id = "__Stellar-Test-DSPSK"
(1) Framed-IP-Address = 192.168.11.100
(1) Framed-IPv6-Address = fe80::cff:a16f:2b7:4c33
(1) Tunnel-Private-Group-Id:0 = "11"
(1) Event-Timestamp = "Sep 8 2020 19:30:53 CEST"
(1) Proxy-State = 0x3133
(1) # Executing section preacct from file /etc/freeradius/3.0/sites-enabled/default
(1) preacct {
(1) [preprocess] = ok
(1) policy acct_unique {
(1) update request {
(1) &Tmp-String-9 := "ai:"
(1) } # update request = noop
(1) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) {
(1) EXPAND %{hex:&Class}
(1) -->
(1) EXPAND ^%{hex:&Tmp-String-9}
(1) --> ^61693a
(1) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) -> FALSE
(1) else {
(1) update request {
(1) EXPAND %{md5:%{User-Name},%{Acct-Session-ID},%{%{NAS-IPv6-Address}:-%{NAS-IP-Address}},%{NAS-Identifier},%{NAS-Port-ID},%{NAS-Port}}
(1) --> 207b4cd53b9808821c90aa7f8971316f
(1) &Acct-Unique-Session-Id := 207b4cd53b9808821c90aa7f8971316f
(1) } # update request = noop
(1) } # else = noop
(1) } # policy acct_unique = noop
(1) suffix: Checking for suffix after "@"
(1) suffix: No '@' in User-Name = "f0:c3:71:2e:fd:8d", looking up realm NULL
(1) suffix: No such realm "NULL"
(1) [suffix] = noop
(1) [files] = noop
(1) } # preacct = ok
(1) # Executing section accounting from file /etc/freeradius/3.0/sites-enabled/default
(1) accounting {
(1) detail: EXPAND /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d
(1) detail: --> /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(1) detail: /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d expands to /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(1) detail: EXPAND %t
(1) detail: --> Tue Sep 8 19:30:53 2020
(1) [detail] = ok
(1) [unix] = ok
(1) [exec] = noop
(1) attr_filter.accounting_response: EXPAND %{User-Name}
(1) attr_filter.accounting_response: --> f0:c3:71:2e:fd:8d
(1) attr_filter.accounting_response: Matched entry DEFAULT at line 12
(1) [attr_filter.accounting_response] = updated
(1) } # accounting = updated
(1) Sent Accounting-Response Id 8 from 192.168.2.134:1813 to 192.168.2.20:1815 length 0
(1) Proxy-State = 0x3133
(1) Finished request
(1) Cleaning up request packet ID 8 with timestamp +27
Ready to process requests
(2) Received Accounting-Request Id 9 from 192.168.2.20:1815 to 192.168.2.134:1813 length 341
(2) Acct-Status-Type = Interim-Update
(2) Acct-Authentic = RADIUS
(2) User-Name = "f0:c3:71:2e:fd:8d"
(2) NAS-IP-Address = 192.168.10.12
(2) NAS-Identifier = "Stellar-Test-DSPSK"
(2) Called-Station-Id = "DC-08-56-13-1E-60:Stellar-Test-DSPSK"
(2) NAS-Port-Type = Wireless-802.11
(2) NAS-Port = 1
(2) NAS-Port-Id = "wifi-5G"
(2) Calling-Station-Id = "F0-C3-71-2E-FD-8D"
(2) Acct-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(2) Acct-Multi-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(2) Filter-Id = "__Stellar-Test-DSPSK"
(2) Framed-IP-Address = 192.168.11.100
(2) Framed-IPv6-Address = fe80::cff:a16f:2b7:4c33
(2) Tunnel-Private-Group-Id:0 = "11"
(2) Acct-Session-Time = 600
(2) Acct-Input-Packets = 1115
(2) Acct-Output-Packets = 759
(2) Acct-Input-Octets = 143198
(2) Acct-Output-Octets = 679342
(2) Event-Timestamp = "Sep 8 2020 19:40:53 CEST"
(2) Proxy-State = 0x3134
(2) # Executing section preacct from file /etc/freeradius/3.0/sites-enabled/default
(2) preacct {
(2) [preprocess] = ok
(2) policy acct_unique {
(2) update request {
(2) &Tmp-String-9 := "ai:"
(2) } # update request = noop
(2) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) {
(2) EXPAND %{hex:&Class}
(2) -->
(2) EXPAND ^%{hex:&Tmp-String-9}
(2) --> ^61693a
(2) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) -> FALSE
(2) else {
(2) update request {
(2) EXPAND %{md5:%{User-Name},%{Acct-Session-ID},%{%{NAS-IPv6-Address}:-%{NAS-IP-Address}},%{NAS-Identifier},%{NAS-Port-ID},%{NAS-Port}}
(2) --> 207b4cd53b9808821c90aa7f8971316f
(2) &Acct-Unique-Session-Id := 207b4cd53b9808821c90aa7f8971316f
(2) } # update request = noop
(2) } # else = noop
(2) } # policy acct_unique = noop
(2) suffix: Checking for suffix after "@"
(2) suffix: No '@' in User-Name = "f0:c3:71:2e:fd:8d", looking up realm NULL
(2) suffix: No such realm "NULL"
(2) [suffix] = noop
(2) [files] = noop
(2) } # preacct = ok
(2) # Executing section accounting from file /etc/freeradius/3.0/sites-enabled/default
(2) accounting {
(2) detail: EXPAND /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d
(2) detail: --> /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(2) detail: /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d expands to /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(2) detail: EXPAND %t
(2) detail: --> Tue Sep 8 19:40:53 2020
(2) [detail] = ok
(2) [unix] = noop
(2) [exec] = noop
(2) attr_filter.accounting_response: EXPAND %{User-Name}
(2) attr_filter.accounting_response: --> f0:c3:71:2e:fd:8d
(2) attr_filter.accounting_response: Matched entry DEFAULT at line 12
(2) [attr_filter.accounting_response] = updated
(2) } # accounting = updated
(2) Sent Accounting-Response Id 9 from 192.168.2.134:1813 to 192.168.2.20:1815 length 0
(2) Proxy-State = 0x3134
(2) Finished request
(2) Cleaning up request packet ID 9 with timestamp +627
Ready to process requests
(3) Received Accounting-Request Id 10 from 192.168.2.20:1815 to 192.168.2.134:1813 length 341
(3) Acct-Status-Type = Interim-Update
(3) Acct-Authentic = RADIUS
(3) User-Name = "f0:c3:71:2e:fd:8d"
(3) NAS-IP-Address = 192.168.10.12
(3) NAS-Identifier = "Stellar-Test-DSPSK"
(3) Called-Station-Id = "DC-08-56-13-1E-60:Stellar-Test-DSPSK"
(3) NAS-Port-Type = Wireless-802.11
(3) NAS-Port = 1
(3) NAS-Port-Id = "wifi-5G"
(3) Calling-Station-Id = "F0-C3-71-2E-FD-8D"
(3) Acct-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(3) Acct-Multi-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(3) Filter-Id = "__Stellar-Test-DSPSK"
(3) Framed-IP-Address = 192.168.11.100
(3) Framed-IPv6-Address = fe80::cff:a16f:2b7:4c33
(3) Tunnel-Private-Group-Id:0 = "11"
(3) Acct-Session-Time = 1200
(3) Acct-Input-Packets = 9735
(3) Acct-Output-Packets = 7867
(3) Acct-Input-Octets = 1557365
(3) Acct-Output-Octets = 4693182
(3) Event-Timestamp = "Sep 8 2020 19:50:53 CEST"
(3) Proxy-State = 0x3135
(3) # Executing section preacct from file /etc/freeradius/3.0/sites-enabled/default
(3) preacct {
(3) [preprocess] = ok
(3) policy acct_unique {
(3) update request {
(3) &Tmp-String-9 := "ai:"
(3) } # update request = noop
(3) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) {
(3) EXPAND %{hex:&Class}
(3) -->
(3) EXPAND ^%{hex:&Tmp-String-9}
(3) --> ^61693a
(3) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) -> FALSE
(3) else {
(3) update request {
(3) EXPAND %{md5:%{User-Name},%{Acct-Session-ID},%{%{NAS-IPv6-Address}:-%{NAS-IP-Address}},%{NAS-Identifier},%{NAS-Port-ID},%{NAS-Port}}
(3) --> 207b4cd53b9808821c90aa7f8971316f
(3) &Acct-Unique-Session-Id := 207b4cd53b9808821c90aa7f8971316f
(3) } # update request = noop
(3) } # else = noop
(3) } # policy acct_unique = noop
(3) suffix: Checking for suffix after "@"
(3) suffix: No '@' in User-Name = "f0:c3:71:2e:fd:8d", looking up realm NULL
(3) suffix: No such realm "NULL"
(3) [suffix] = noop
(3) [files] = noop
(3) } # preacct = ok
(3) # Executing section accounting from file /etc/freeradius/3.0/sites-enabled/default
(3) accounting {
(3) detail: EXPAND /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d
(3) detail: --> /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(3) detail: /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d expands to /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(3) detail: EXPAND %t
(3) detail: --> Tue Sep 8 19:50:54 2020
(3) [detail] = ok
(3) [unix] = noop
(3) [exec] = noop
(3) attr_filter.accounting_response: EXPAND %{User-Name}
(3) attr_filter.accounting_response: --> f0:c3:71:2e:fd:8d
(3) attr_filter.accounting_response: Matched entry DEFAULT at line 12
(3) [attr_filter.accounting_response] = updated
(3) } # accounting = updated
(3) Sent Accounting-Response Id 10 from 192.168.2.134:1813 to 192.168.2.20:1815 length 0
(3) Proxy-State = 0x3135
(3) Finished request
(3) Cleaning up request packet ID 10 with timestamp +1228
Ready to process requests
(4) Received Accounting-Request Id 11 from 192.168.2.20:1815 to 192.168.2.134:1813 length 341
(4) Acct-Status-Type = Interim-Update
(4) Acct-Authentic = RADIUS
(4) User-Name = "f0:c3:71:2e:fd:8d"
(4) NAS-IP-Address = 192.168.10.12
(4) NAS-Identifier = "Stellar-Test-DSPSK"
(4) Called-Station-Id = "DC-08-56-13-1E-60:Stellar-Test-DSPSK"
(4) NAS-Port-Type = Wireless-802.11
(4) NAS-Port = 1
(4) NAS-Port-Id = "wifi-5G"
(4) Calling-Station-Id = "F0-C3-71-2E-FD-8D"
(4) Acct-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(4) Acct-Multi-Session-Id = "192.168.10.12_08/09/2020_19:30:46_f0c3712efd8d"
(4) Filter-Id = "__Stellar-Test-DSPSK"
(4) Framed-IP-Address = 192.168.11.100
(4) Framed-IPv6-Address = fe80::cff:a16f:2b7:4c33
(4) Tunnel-Private-Group-Id:0 = "11"
(4) Acct-Session-Time = 1800
(4) Acct-Input-Packets = 10854
(4) Acct-Output-Packets = 8489
(4) Acct-Input-Octets = 1698748
(4) Acct-Output-Octets = 4990413
(4) Event-Timestamp = "Sep 8 2020 20:00:53 CEST"
(4) Proxy-State = 0x3136
(4) # Executing section preacct from file /etc/freeradius/3.0/sites-enabled/default
(4) preacct {
(4) [preprocess] = ok
(4) policy acct_unique {
(4) update request {
(4) &Tmp-String-9 := "ai:"
(4) } # update request = noop
(4) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) {
(4) EXPAND %{hex:&Class}
(4) -->
(4) EXPAND ^%{hex:&Tmp-String-9}
(4) --> ^61693a
(4) if (("%{hex:&Class}" =~ /^%{hex:&Tmp-String-9}/) && ("%{string:&Class}" =~ /^ai:([0-9a-f]{32})/i)) -> FALSE
(4) else {
(4) update request {
(4) EXPAND %{md5:%{User-Name},%{Acct-Session-ID},%{%{NAS-IPv6-Address}:-%{NAS-IP-Address}},%{NAS-Identifier},%{NAS-Port-ID},%{NAS-Port}}
(4) --> 207b4cd53b9808821c90aa7f8971316f
(4) &Acct-Unique-Session-Id := 207b4cd53b9808821c90aa7f8971316f
(4) } # update request = noop
(4) } # else = noop
(4) } # policy acct_unique = noop
(4) suffix: Checking for suffix after "@"
(4) suffix: No '@' in User-Name = "f0:c3:71:2e:fd:8d", looking up realm NULL
(4) suffix: No such realm "NULL"
(4) [suffix] = noop
(4) [files] = noop
(4) } # preacct = ok
(4) # Executing section accounting from file /etc/freeradius/3.0/sites-enabled/default
(4) accounting {
(4) detail: EXPAND /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d
(4) detail: --> /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(4) detail: /var/log/freeradius/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d expands to /var/log/freeradius/radacct/192.168.2.20/detail-20200908
(4) detail: EXPAND %t
(4) detail: --> Tue Sep 8 20:00:53 2020
(4) [detail] = ok
(4) [unix] = noop
(4) [exec] = noop
(4) attr_filter.accounting_response: EXPAND %{User-Name}
(4) attr_filter.accounting_response: --> f0:c3:71:2e:fd:8d
(4) attr_filter.accounting_response: Matched entry DEFAULT at line 12
(4) [attr_filter.accounting_response] = updated
(4) } # accounting = updated
(4) Sent Accounting-Response Id 11 from 192.168.2.134:1813 to 192.168.2.20:1815 length 0
(4) Proxy-State = 0x3136
(4) Finished request
(4) Cleaning up request packet ID 11 with timestamp +1827
Ready to process requests
Konfiguration für Stellar Wireless / OmniVista
Einrichtung der Stellar Wireless DSPSK SSID
Wichtig ist in diesem Schritt den OmniVista UPAM Radius Eintrag auszuwählen, damit die Stellar Wireless APs sich an OmniVista UPAM und nicht direkt an den Radius wenden. Die Konfiguration kann bereits auf die gewünschte AP-Gruppe ausgerollt werden!
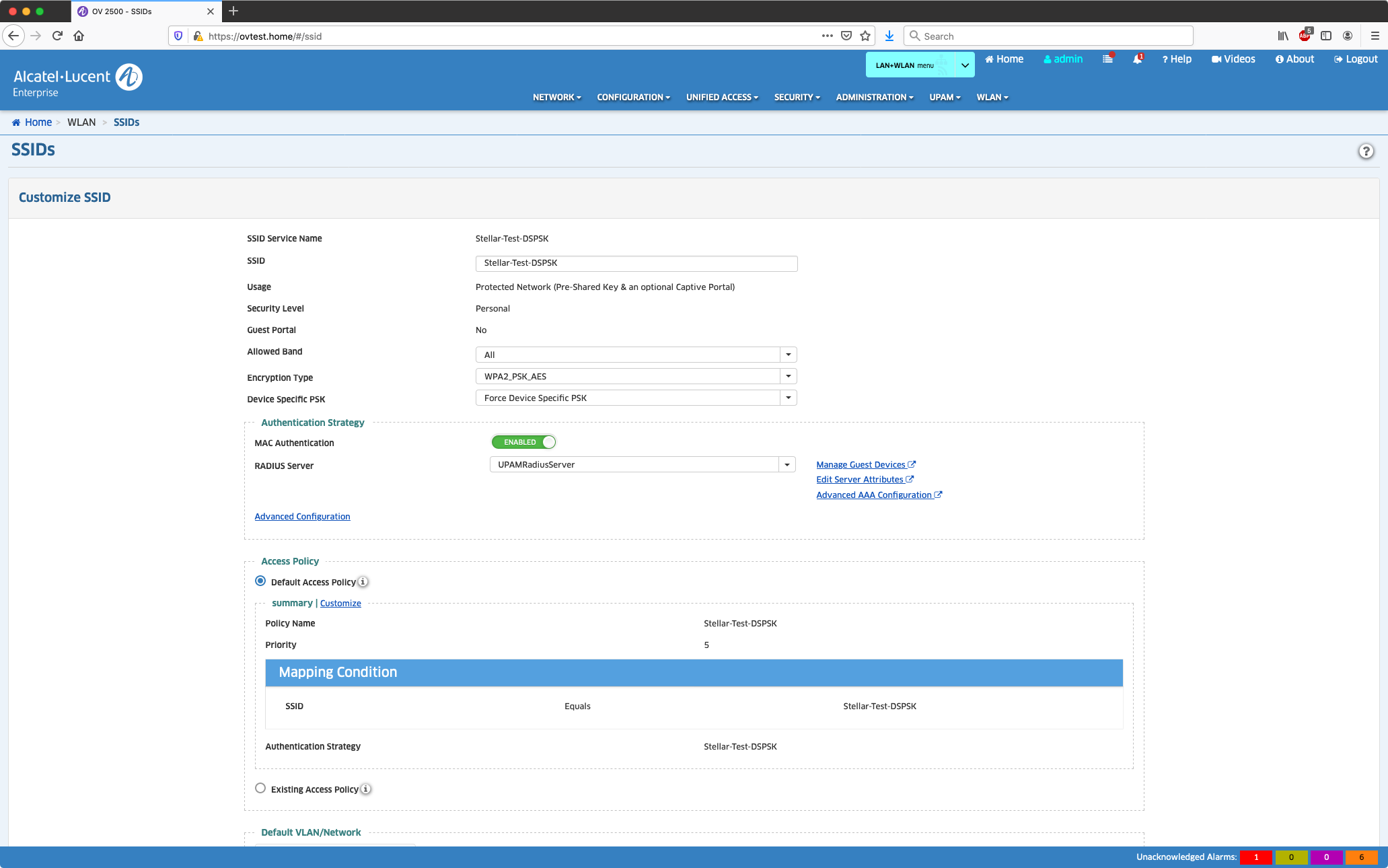
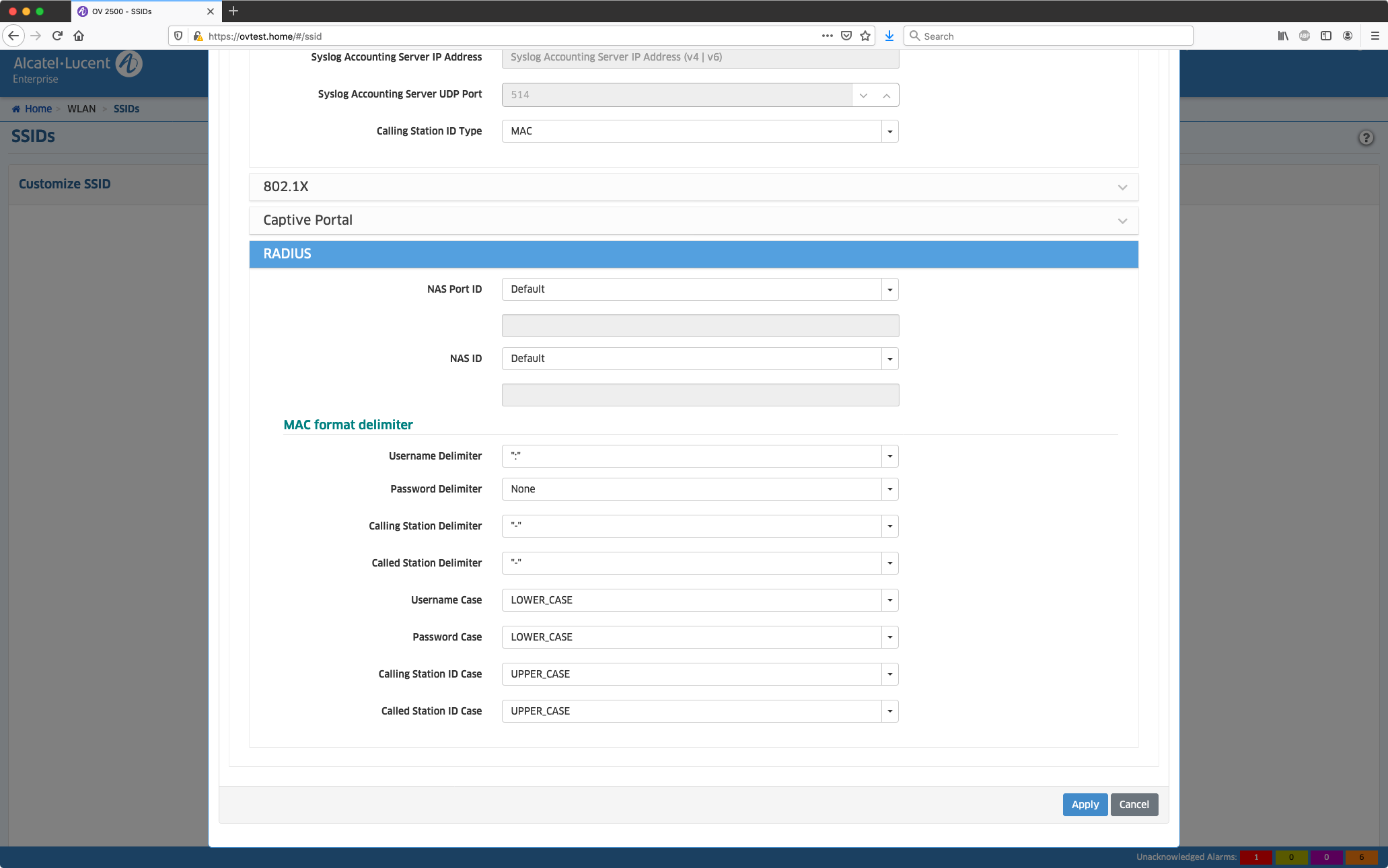
Optional: Granulare Konfiguration der "Advanced AAA Configuration"
Hier kann wahlweise das Format für die Anfrage am RADIUS festgelegt werden. OV 4.5R2 (>= Build 63) wird den Access-Request entsprechend durchleiten.
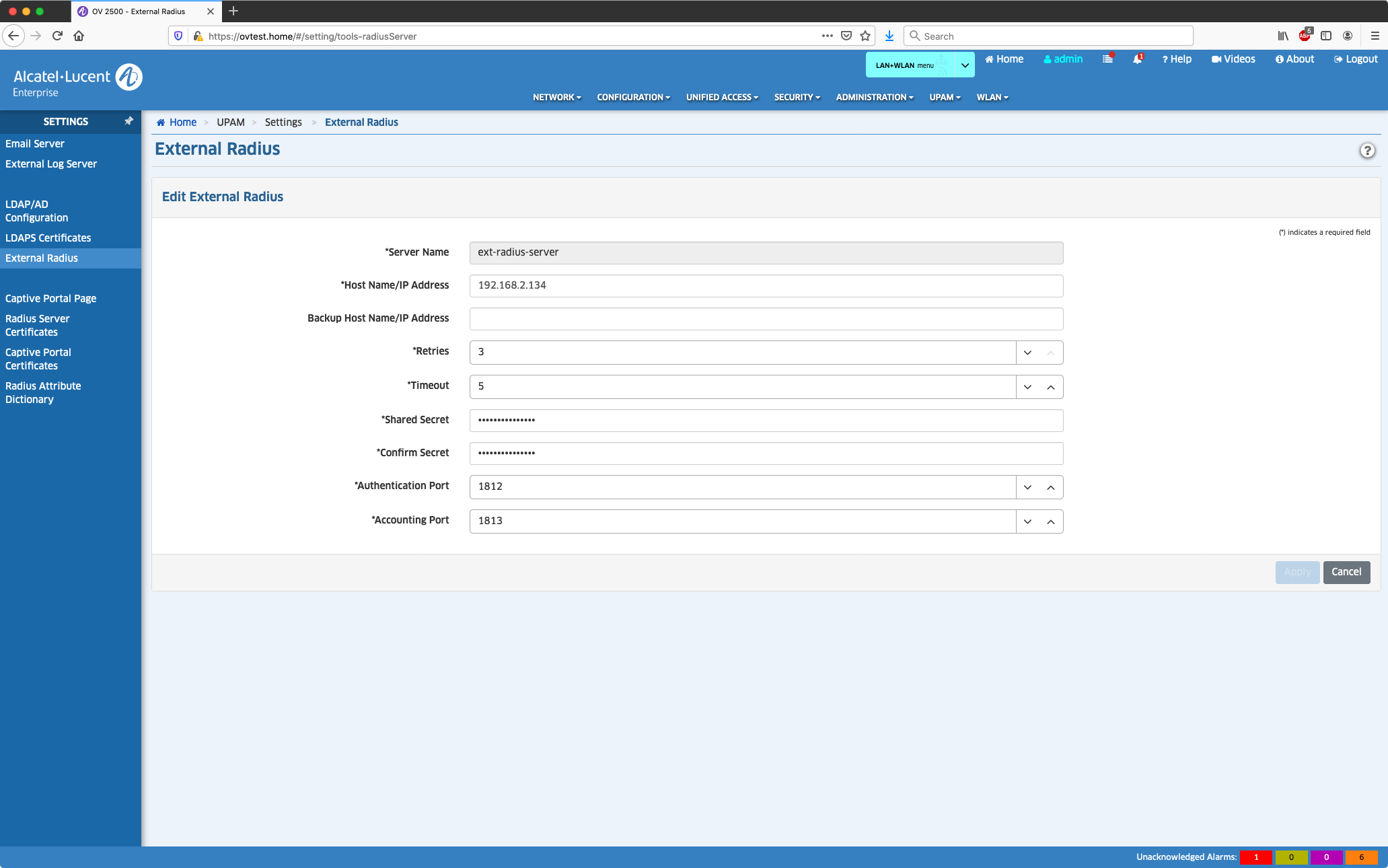
Externen Radius-Server anlegen
Dies ist der externe Radius-Server mit einem eigenen Radius Shared Secret (hier sollte man von meinem Beispiel „ext-radius-2020“ abweichen)!
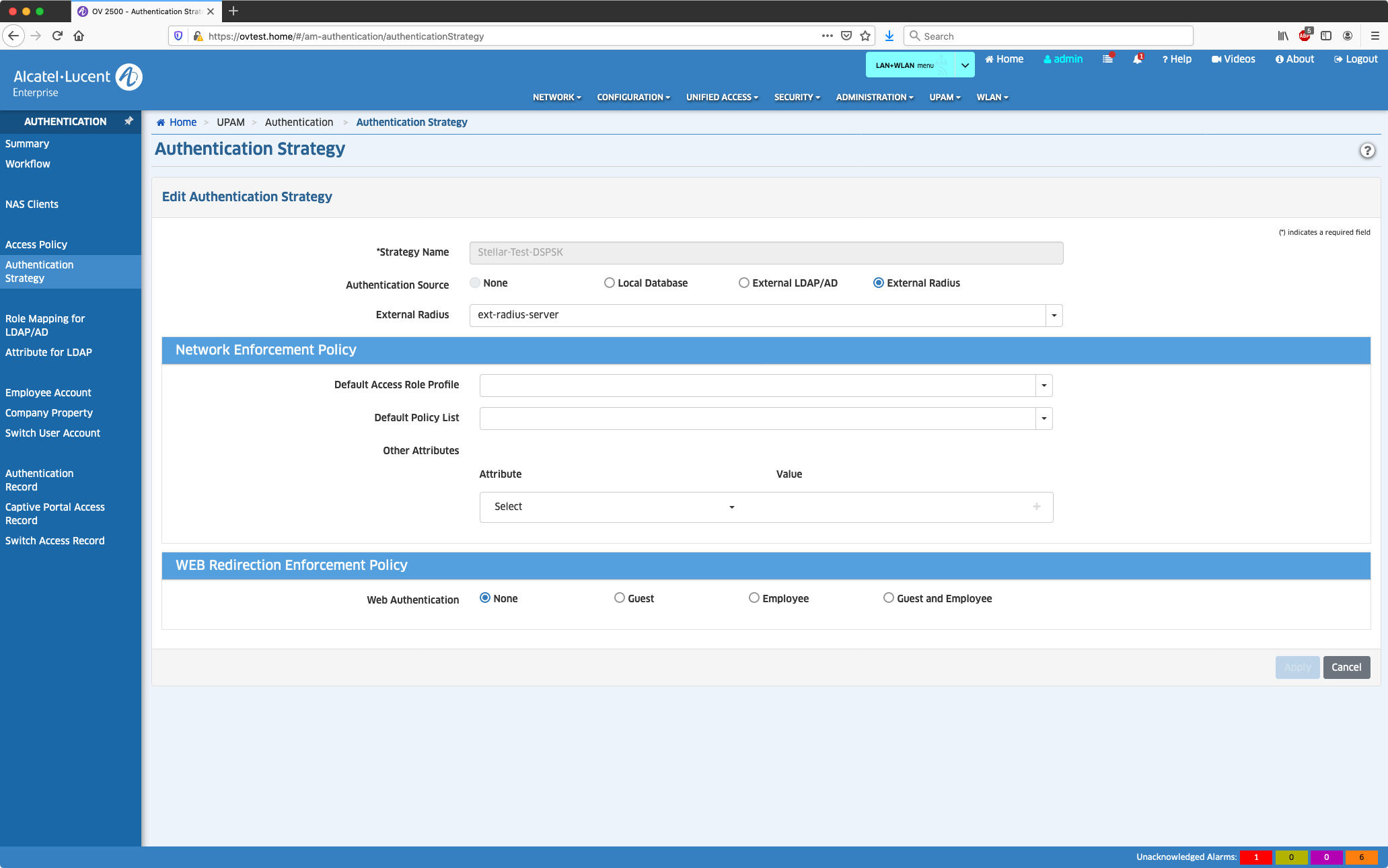
Bestehende "Authentication Strategy" editieren
Die bereits im Rahmen der SSID-Erzeugung angelegte Authentication Strategy ändert man nun von Local Database auf den soeben angelegten External Radius.
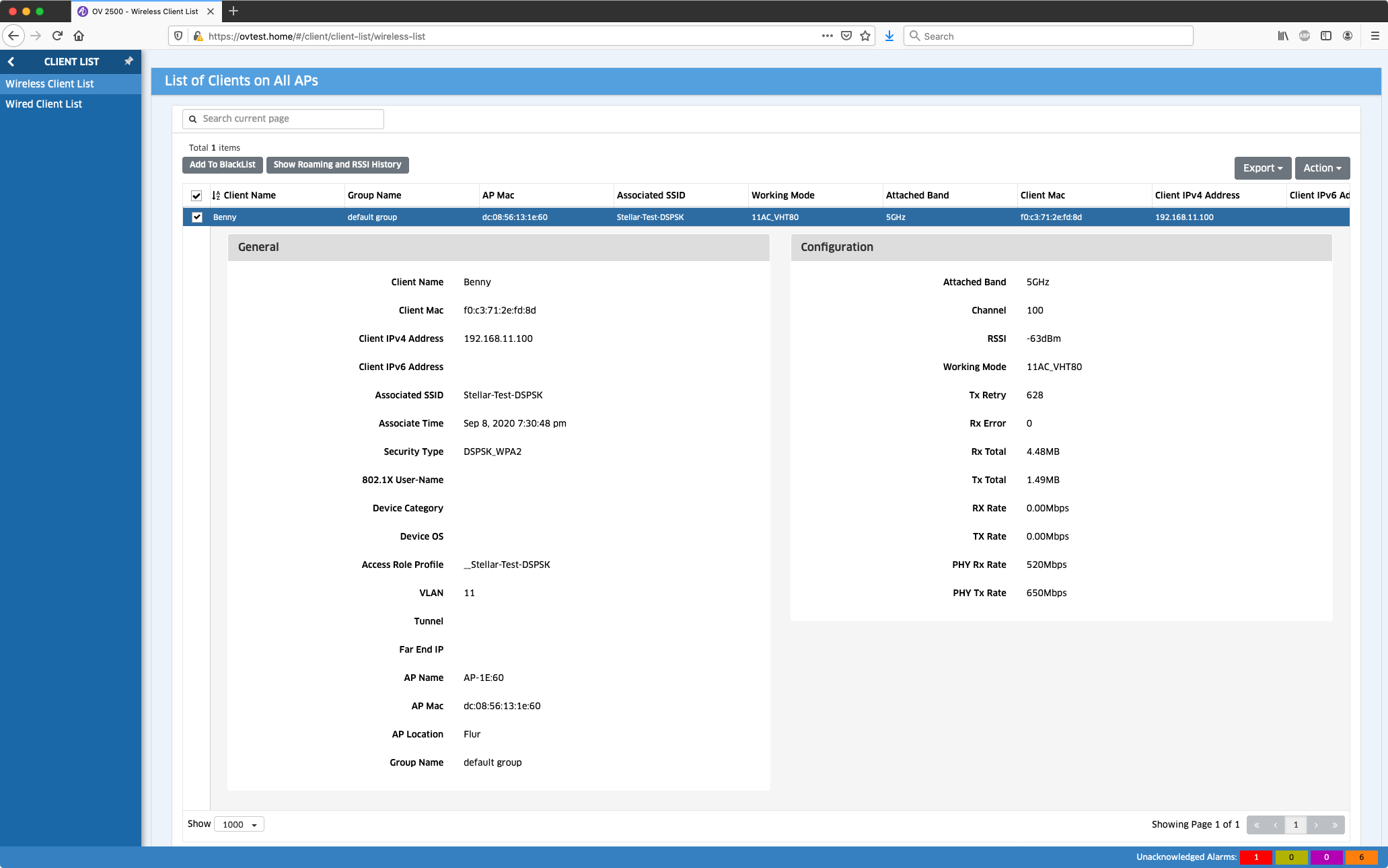
Prüfen der Installation
OmniVista: Client List
Wireshark zur Analyse der RADIUS-Kommunikation
Wireshark Capture meines Laboraufbaus: dspsk3.pcapng.zip (Radius Shared Secret: ext-radius-2020)
Im folgenden Screenshot wird gezeigt über welches Menü man den Key in Wireshark hinterlegen kann.