stellar-wireless-wpa3-sae-raspberry-pi
Dies ist eine alte Version des Dokuments!
Inhaltsverzeichnis
How to connect Raspberry Pi 3 B+ with WPA3-Personal (SAE/PMF) to Stellar Wireless AP
Connecting with WPA3-Personal (SAE/PMF) on the Raspberry Pi 3 B+ via on-board wireless NIC is not exactly straight forward, but it works. On this page I'll document what needs to be done, to get it to work.
Equipement & Access Point used:
- Alcatel-Lucent Enterprise Stellar Wireless AP1201
- AWOS v3.0.6.20
- OmniVista 2500 v4.4R1 Build 39
- Raspberry Pi Model 3 B+
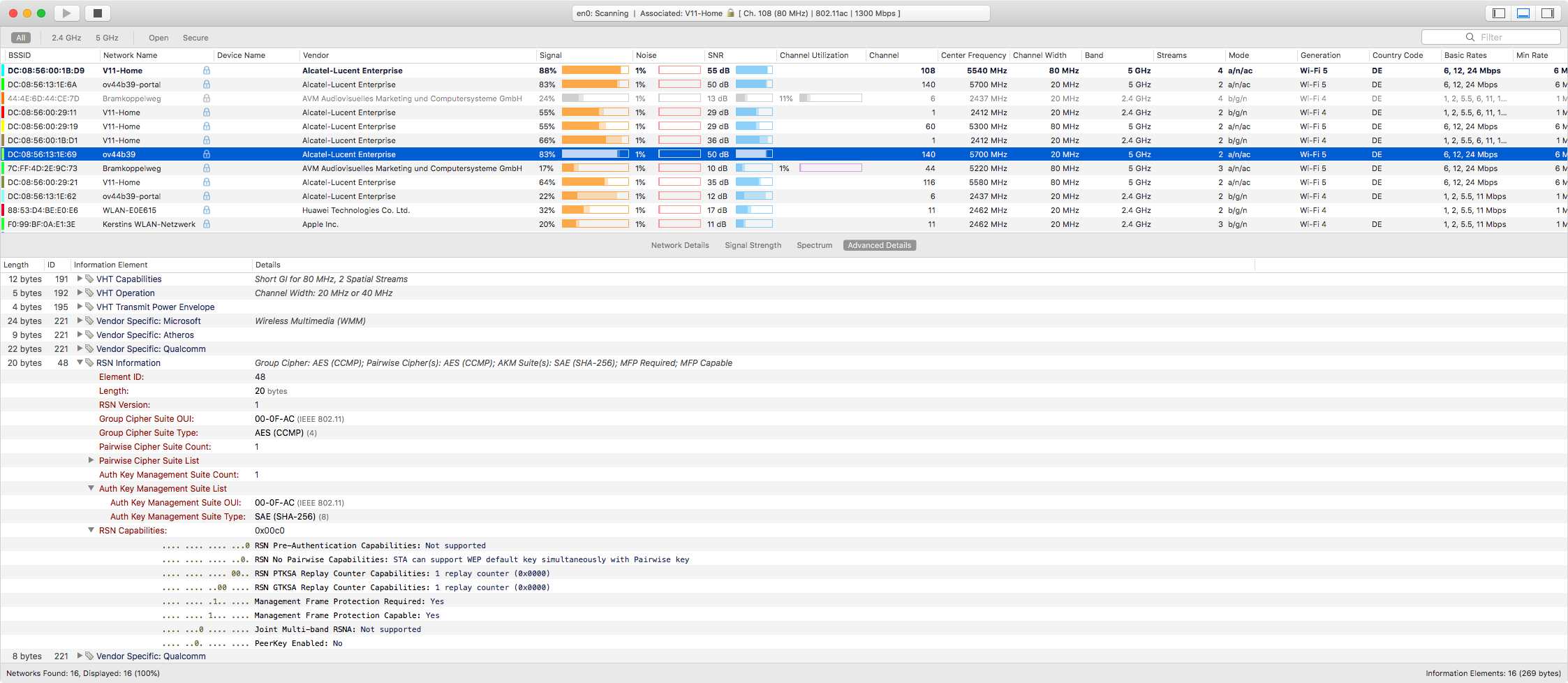
Connecting to SSID „ov44b39“ mandates MFP/PMF (as SAE-only), as you can tell from following Wifi Explorer screenshot.
PCAP Screenshot
 Download of the PCAP (check #152): ch140_2019-05-18_01.07.31.pcap.zip
Download of the PCAP (check #152): ch140_2019-05-18_01.07.31.pcap.zip
SSID Overview (get_wlan)
support@AP-1E:60:/tmp$ ssudo wam_debug get_wlan
{
[
{
"srvname": "ov44b39-portal",
"ssid": "ov44b39-portal",
"hide": "no",
"ssid_enable": "enable",
"band": "all",
"seclevel": "psk",
"encryptype": "wpa3_psk_sae_aes",
"ifindex": "2g: ath02, 5g_1: ath12, 5g_2: ",
"passphrase": "******",
"prekey": "******",
"AAAprofile": "ov44b39-portal",
"macau_enable": "enable",
"bypass_enable": "disable",
"mac_eap_allow": "enable",
"macpassrole": "",
"classification_enable": "disable",
"defaultrole": "__ov44b39-portal",
"80211r_enable": "disable",
"okc_enable": "disable",
"l3_roaming": "disable",
"bcrotation_enable": "disable",
"bcrotation_inteval": 15,
"mesh": "disable",
"clientIsolation": "disable"
},
{
"srvname": "ov44b39",
"ssid": "ov44b39",
"hide": "no",
"ssid_enable": "enable",
"band": "all",
"seclevel": "psk",
"encryptype": "wpa3_sae_aes",
"ifindex": "2g: ath01, 5g_1: ath11, 5g_2: ",
"passphrase": "******",
"prekey": "******",
"AAAprofile": "",
"macau_enable": "disable",
"bypass_enable": "disable",
"mac_eap_allow": "enable",
"macpassrole": "",
"classification_enable": "disable",
"defaultrole": "__ov44b39",
"80211r_enable": "disable",
"okc_enable": "disable",
"l3_roaming": "disable",
"bcrotation_enable": "disable",
"bcrotation_inteval": 15,
"mesh": "disable",
"clientIsolation": "disable"
}
]
}
Client Overview (sta_list)
support@AP-1E:60:/tmp$ ssudo wam_debug sta_list
{
"status": "Success!!!",
"wlanServiceData": [
{
"iface": "ath02",
"ssid": "ov44b39-portal",
"freq": "2.4GHz",
"security": "Personal(WPA3_PSK_SAE_AES)",
"wlanService": "ov44b39-portal"
},
{
"iface": "ath12",
"ssid": "ov44b39-portal",
"freq": "5GHz",
"security": "Personal(WPA3_PSK_SAE_AES)",
"wlanService": "ov44b39-portal"
},
{
"iface": "ath01",
"ssid": "ov44b39",
"freq": "2.4GHz",
"security": "Personal(WPA3_SAE_AES)",
"wlanService": "ov44b39"
},
{
"iface": "ath11",
"ssid": "ov44b39",
"freq": "5GHz",
"security": "Personal(WPA3_SAE_AES)",
"wlanService": "ov44b39",
"staData": [
{
"staMAC": "b8:27:eb:ea:8c:42",
"staIP": "192.168.12.115",
"staGlobalIPv6": "::",
"staLocalIPv6": "fe80::13de:b443:e411:7bc7",
"associationTime": 847,
"mappingType": 0,
"assignedVLAN": 12,
"assignedAR": "__ov44b39",
"assignedPL": "",
"macAuthResult": "",
"ARFromMACAuth": "",
"PLFromMACAuth": "",
"redirectURLFromMACAuth": "",
"ARFrom8021xAuth": "",
"PLFrom8021xAuth": "",
"redirectURLFrom8021xAuth": "",
"CPAuthResult": "FAILED",
"ARFromCPAuth": "",
"PLFromCPAuth": "",
"ARFromRoaming": "",
"PLFromRoaming": "",
"redirectURLFromRoaming": "",
"classificationMatched": "none"
}
]
}
]
}
Client Overview (wlanconfig ath11 list)
I still need to figure out a few things and configure the Pi for some proper 11ac stuff.
support@AP-1E:60:/tmp$ wlanconfig ath11 list ADDR AID CHAN TXRATE RXRATE RSSI MINRSSI MAXRSSI IDLE TXSEQ RXSEQ CAPS XCAPS ACAPS ERP STATE MAXRATE(DOT11) HTCAPS VHTCAPS ASSOCTIME IEs MODE PSMODE RXNSS TXNSS b8:27:eb:ea:8c:42 1 140 6M 65M 63 62 75 15 0 65535 EP ORIf 0 b 0 AQ 10g 00:15:24 RSN WME IEEE80211_MODE_11NA_HT20 0 1 1 Minimum Tx Power : 3 Maximum Tx Power : 20 HT Capability : Yes VHT Capability : No MU capable : No SNR : 63 Operating band : 5GHz Current Operating class : 0 Supported Rates : 12 18 24 36 48 72 96 108
Output from Raspberry Pi (wpa_supplicant)
pi@raspberrypi:~/hostap_2_6/wpa_supplicant $ sudo ./wpa_supplicant -c wpa_supplicant.conf -dd -i wlan0
wpa_supplicant v2.6
random: Trying to read entropy from /dev/random
Successfully initialized wpa_supplicant
Initializing interface 'wlan0' conf 'wpa_supplicant.conf' driver 'default' ctrl_interface 'N/A' bridge 'N/A'
Configuration file 'wpa_supplicant.conf' -> '/home/pi/hostap_2_6/wpa_supplicant/wpa_supplicant.conf'
Reading configuration file '/home/pi/hostap_2_6/wpa_supplicant/wpa_supplicant.conf'
ctrl_interface='DIR=/var/run/wpa_supplicant GROUP=netdev'
eapol_version=1
ap_scan=1
fast_reauth=1
country='DE'
pmf=1
Line: 1947 - start of a new network block
ssid - hexdump_ascii(len=7):
6f 76 34 34 62 33 39 ov44b39
proto: 0x2
key_mgmt: 0x400
sae_password - hexdump_ascii(len=8): [REMOVED]
Priority group 0
id=0 ssid='ov44b39'
nl80211: Supported cipher 00-0f-ac:1
nl80211: Supported cipher 00-0f-ac:5
nl80211: Supported cipher 00-0f-ac:2
nl80211: Supported cipher 00-0f-ac:4
nl80211: Supported cipher 00-0f-ac:6
nl80211: Using driver-based off-channel TX
nl80211: Supported vendor command: vendor_id=0x1018 subcmd=1
nl80211: Supported vendor event: vendor_id=0x1018 subcmd=0
nl80211: Use separate P2P group interface (driver advertised support)
nl80211: Enable multi-channel concurrent (driver advertised support)
nl80211: use P2P_DEVICE support
nl80211: interface wlan0 in phy phy0
nl80211: Set mode ifindex 3 iftype 2 (STATION)
nl80211: Subscribe to mgmt frames with non-AP handle 0x1338538
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0801
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=06
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0a07
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0a11
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=1101
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=1102
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0505
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0500
rfkill: initial event: idx=0 type=1 op=0 soft=0 hard=0
netlink: Operstate: ifindex=3 linkmode=1 (userspace-control), operstate=5 (IF_OPER_DORMANT)
Add interface wlan0 to a new radio phy0
nl80211: Regulatory information - country=DE (DFS-ETSI)
nl80211: 2400-2483 @ 40 MHz 20 mBm
nl80211: 5150-5250 @ 80 MHz 20 mBm (no outdoor)
nl80211: 5250-5350 @ 80 MHz 20 mBm (no outdoor) (DFS)
nl80211: 5470-5725 @ 160 MHz 26 mBm (DFS)
nl80211: 5725-5875 @ 80 MHz 13 mBm
nl80211: 57000-66000 @ 2160 MHz 40 mBm
nl80211: Added 802.11b mode based on 802.11g information
wlan0: Own MAC address: b8:27:eb:ea:8c:42
wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=(nil) key_idx=0 set_tx=0 seq_len=0 key_len=0
wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=(nil) key_idx=1 set_tx=0 seq_len=0 key_len=0
wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=(nil) key_idx=2 set_tx=0 seq_len=0 key_len=0
wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=(nil) key_idx=3 set_tx=0 seq_len=0 key_len=0
wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=(nil) key_idx=4 set_tx=0 seq_len=0 key_len=0
wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=(nil) key_idx=5 set_tx=0 seq_len=0 key_len=0
wlan0: RSN: flushing PMKID list in the driver
nl80211: Flush PMKIDs
ENGINE: Loading dynamic engine
ENGINE: Loading dynamic engine
EAPOL: SUPP_PAE entering state DISCONNECTED
EAPOL: Supplicant port status: Unauthorized
nl80211: Skip set_supp_port(unauthorized) while not associated
EAPOL: KEY_RX entering state NO_KEY_RECEIVE
EAPOL: SUPP_BE entering state INITIALIZE
EAP: EAP entering state DISABLED
ctrl_interface_group=108 (from group name 'netdev')
wlan0: Added interface wlan0
wlan0: State: DISCONNECTED -> DISCONNECTED
nl80211: Set wlan0 operstate 0->0 (DORMANT)
netlink: Operstate: ifindex=3 linkmode=-1 (no change), operstate=5 (IF_OPER_DORMANT)
random: Got 20/20 bytes from /dev/random
RTM_NEWLINK: ifi_index=3 ifname=wlan0 operstate=2 linkmode=0 ifi_family=0 ifi_flags=0x1003 ([UP])
RTM_NEWLINK: ifi_index=3 ifname=wlan0 operstate=2 linkmode=1 ifi_family=0 ifi_flags=0x1003 ([UP])
wlan0: Starting delayed sched scan
wlan0: Use normal scan instead of sched_scan for initial scans (normal_scans=0)
wlan0: Setting scan request: 0.000000 sec
wlan0: State: DISCONNECTED -> SCANNING
wlan0: Starting AP scan for wildcard SSID
wlan0: Add radio work 'scan'@0x1348f90
wlan0: First radio work item in the queue - schedule start immediately
wlan0: Starting radio work 'scan'@0x1348f90 after 0.000653 second wait
wlan0: nl80211: scan request
nl80211: Scan SSID - hexdump_ascii(len=0): [NULL]
Scan requested (ret=0) - scan timeout 10 seconds
nl80211: Event message available
nl80211: Drv Event 33 (NL80211_CMD_TRIGGER_SCAN) received for wlan0
wlan0: nl80211: Scan trigger
wlan0: Event SCAN_STARTED (47) received
wlan0: Own scan request started a scan in 0.001780 seconds
EAPOL: disable timer tick
RTM_NEWLINK: ifi_index=3 ifname=wlan0 wext ifi_family=0 ifi_flags=0x1003 ([UP])
nl80211: Event message available
nl80211: Drv Event 34 (NL80211_CMD_NEW_SCAN_RESULTS) received for wlan0
wlan0: nl80211: New scan results available
nl80211: Scan probed for SSID ''
nl80211: Scan included frequencies: 2412 2417 2422 2427 2432 2437 2442 2447 2452 2457 2462 2467 2472 5180 5200 5220 5240 5260 5280 5300 5320 5500 5520 5540 5560 5580 5600 5620 5640 5660 5680 5700
wlan0: Event SCAN_RESULTS (3) received
wlan0: Scan completed in 2.390465 seconds
nl80211: Received scan results (19 BSSes)
wlan0: BSS: Start scan result update 1
wlan0: BSS: Add new id 0 BSSID dc:08:56:00:1b:d9 SSID 'V11-Home' freq 5540
wlan0: BSS: Add new id 1 BSSID dc:08:56:00:29:19 SSID 'V11-Home' freq 5300
wlan0: BSS: Add new id 2 BSSID dc:08:56:00:29:21 SSID 'V11-Home' freq 5580
wlan0: BSS: Add new id 3 BSSID dc:08:56:13:1e:69 SSID 'ov44b39' freq 5700
wlan0: BSS: Add new id 4 BSSID dc:08:56:13:1e:6a SSID 'ov44b39-portal' freq 5700
wlan0: BSS: Add new id 5 BSSID dc:08:56:00:1b:d1 SSID 'V11-Home' freq 2412
wlan0: BSS: Add new id 6 BSSID dc:08:56:13:1e:61 SSID 'ov44b39' freq 2437
wlan0: BSS: Add new id 7 BSSID dc:08:56:13:1e:62 SSID 'ov44b39-portal' freq 2437
wlan0: BSS: Add new id 8 BSSID 6c:f3:7f:77:08:01 SSID 'ALU4U-Mobility' freq 2462
wlan0: BSS: Add new id 9 BSSID dc:08:56:00:29:11 SSID 'V11-Home' freq 2412
wlan0: BSS: Add new id 10 BSSID 44:4e:6d:44:ce:7d SSID 'Bramkoppelweg' freq 2437
wlan0: BSS: Add new id 11 BSSID 88:53:d4:be:e0:e6 SSID 'WLAN-E0E615' freq 2462
wlan0: BSS: Add new id 12 BSSID d4:21:22:de:da:33 SSID 'WLAN-633353' freq 2412
wlan0: BSS: Add new id 13 BSSID 7c:ff:4d:2e:9c:73 SSID 'Bramkoppelweg' freq 5220
wlan0: BSS: Add new id 14 BSSID 90:67:1c:ef:2f:d2 SSID 'WLAN-WD57L2' freq 2452
wlan0: BSS: Add new id 15 BSSID f0:99:bf:0a:e1:3e SSID 'Kerstins WLAN-Netzwerk' freq 2462
wlan0: BSS: Add new id 16 BSSID 44:4e:6d:44:ce:7c SSID 'Bramkoppelweg' freq 5220
wlan0: BSS: Add new id 17 BSSID 90:67:1c:ef:2f:d3 SSID 'Telekom_FON' freq 2452
wlan0: BSS: Add new id 18 BSSID 2e:3a:e8:15:8e:ad SSID 'ECOVACS_0532' freq 2412
BSS: last_scan_res_used=19/32
wlan0: New scan results available (own=1 ext=0)
wlan0: Radio work 'scan'@0x1348f90 done in 2.430070 seconds
wlan0: radio_work_free('scan'@0x1348f90: num_active_works --> 0
wlan0: Selecting BSS from priority group 0
wlan0: 0: dc:08:56:00:1b:d9 ssid='V11-Home' wpa_ie_len=0 rsn_ie_len=20 caps=0x1511 level=-30 freq=5540
wlan0: skip - SSID mismatch
wlan0: 1: dc:08:56:00:29:19 ssid='V11-Home' wpa_ie_len=0 rsn_ie_len=20 caps=0x1511 level=-49 freq=5300
wlan0: skip - SSID mismatch
wlan0: 2: dc:08:56:00:29:21 ssid='V11-Home' wpa_ie_len=0 rsn_ie_len=20 caps=0x1511 level=-51 freq=5580
wlan0: skip - SSID mismatch
wlan0: 3: dc:08:56:13:1e:69 ssid='ov44b39' wpa_ie_len=0 rsn_ie_len=20 caps=0x511 level=-13 freq=5700
wlan0: selected based on RSN IE
wlan0: selected BSS dc:08:56:13:1e:69 ssid='ov44b39'
wlan0: Considering connect request: reassociate: 0 selected: dc:08:56:13:1e:69 bssid: 00:00:00:00:00:00 pending: 00:00:00:00:00:00 wpa_state: SCANNING ssid=0x1339468 current_ssid=(nil)
wlan0: Request association with dc:08:56:13:1e:69
wlan0: Add radio work 'connect'@0x1348f90
wlan0: First radio work item in the queue - schedule start immediately
wlan0: Starting radio work 'connect'@0x1348f90 after 0.000208 second wait
wlan0: Trying to associate with dc:08:56:13:1e:69 (SSID='ov44b39' freq=5700 MHz)
wlan0: Cancelling scan request
wlan0: WPA: clearing own WPA/RSN IE
wlan0: Automatic auth_alg selection: 0x1
RSN: PMKSA cache search - network_ctx=0x1339468 try_opportunistic=0
RSN: Search for BSSID dc:08:56:13:1e:69
RSN: No PMKSA cache entry found
wlan0: RSN: using IEEE 802.11i/D9.0
wlan0: WPA: Selected cipher suites: group 16 pairwise 16 key_mgmt 1024 proto 2
wlan0: WPA: Selected mgmt group cipher 32
wlan0: WPA: clearing AP WPA IE
WPA: set AP RSN IE - hexdump(len=22): 30 14 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 08 c0 00
wlan0: WPA: using GTK CCMP
wlan0: WPA: using PTK CCMP
wlan0: RSN: using KEY_MGMT SAE
wlan0: WPA: using MGMT group cipher AES-128-CMAC
WPA: Set own WPA IE default - hexdump(len=28): 30 1a 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 08 80 00 00 00 00 0f ac 06
wlan0: State: SCANNING -> ASSOCIATING
nl80211: Set wlan0 operstate 0->0 (DORMANT)
netlink: Operstate: ifindex=3 linkmode=-1 (no change), operstate=5 (IF_OPER_DORMANT)
Limit connection to BSSID dc:08:56:13:1e:69 freq=5700 MHz based on scan results (bssid_set=0)
wlan0: WPA: Selected AP supports MFP: require MFP
nl80211: Set mode ifindex 3 iftype 2 (STATION)
nl80211: Unsubscribe mgmt frames handle 0x89bb0db1 (mode change)
nl80211: Subscribe to mgmt frames with non-AP handle 0x1338538
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0801
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=06
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0a07
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0a11
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=1101
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=1102
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0505
nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0x1338538 match=0500
nl80211: Connect (ifindex=3)
* bssid=dc:08:56:13:1e:69
* bssid_hint=dc:08:56:13:1e:69
* freq=5700
* freq_hint=5700
* SSID - hexdump_ascii(len=7):
6f 76 34 34 62 33 39 ov44b39
* IEs - hexdump(len=28): 30 1a 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 08 80 00 00 00 00 0f ac 06
* WPA Versions 0x4
* pairwise=0xfac04
* group=0xfac04
* akm=0xfac08
* SAE password - hexdump_ascii(len=8): [REMOVED]
* Auth Type 4
nl80211: Connect request send successfully
wlan0: Setting authentication timeout: 10 sec 0 usec
EAPOL: External notification - EAP success=0
EAPOL: External notification - EAP fail=0
EAPOL: External notification - portControl=Auto
RTM_NEWLINK: ifi_index=3 ifname=wlan0 operstate=5 linkmode=1 ifi_family=0 ifi_flags=0x11003 ([UP][LOWER_UP])
RTM_NEWLINK: ifi_index=3 ifname=wlan0 wext ifi_family=0 ifi_flags=0x11003 ([UP][LOWER_UP])
RTM_NEWLINK: ifi_index=3 ifname=wlan0 wext ifi_family=0 ifi_flags=0x11003 ([UP][LOWER_UP])
RTM_NEWLINK: ifi_index=3 ifname=wlan0 wext ifi_family=0 ifi_flags=0x11003 ([UP][LOWER_UP])
nl80211: Event message available
nl80211: Drv Event 46 (NL80211_CMD_CONNECT) received for wlan0
nl80211: Connect event (status=0 ignore_next_local_disconnect=0)
nl80211: Associated on 5700 MHz
nl80211: Associated with dc:08:56:13:1e:69
nl80211: Operating frequency for the associated BSS from scan results: 5700 MHz
wlan0: Event ASSOC (0) received
wlan0: Association info event
req_ies - hexdump(len=133): 00 07 6f 76 34 34 62 33 39 01 08 8c 12 98 24 b0 48 60 6c 21 02 03 14 24 06 24 04 34 04 64 0b 30 26 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 08 cc 00 01 00 6d bb 3b a2 09 10 22 9e d9 af 7e 9b 57 65 5f 67 2d 1a 21 00 17 ff 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 7f 08 00 00 00 00 00 00 00 40 dd 09 00 10 18 02 00 00 10 00 00 dd 07 00 50 f2 02 00 01 00 ff 00 00 00
resp_ies - hexdump(len=114): 01 08 8c 12 98 24 b0 48 60 6c 2d 1a ad 09 03 ff ff 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 00 00 00 3d 16 8c 00 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 7f 08 04 00 00 02 00 00 00 40 dd 18 00 50 f2 02 01 01 80 00 03 a4 00 00 27 a4 00 00 42 43 5e 00 62 32 2f 00 dd 08 8c fd f0 01 01 02 01 00 00 00 00 00 00 00
wlan0: freq=5700 MHz
WPA: set own WPA/RSN IE - hexdump(len=40): 30 26 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 08 cc 00 01 00 6d bb 3b a2 09 10 22 9e d9 af 7e 9b 57 65 5f 67
RSN: PMKSA cache search - network_ctx=(nil) try_opportunistic=0
RSN: Search for PMKID - hexdump(len=16): 6d bb 3b a2 09 10 22 9e d9 af 7e 9b 57 65 5f 67
RSN: No PMKSA cache entry found
wlan0: RSN: PMKID from assoc IE not found from PMKSA cache
wlan0: State: ASSOCIATING -> ASSOCIATED
nl80211: Set wlan0 operstate 0->0 (DORMANT)
netlink: Operstate: ifindex=3 linkmode=-1 (no change), operstate=5 (IF_OPER_DORMANT)
wlan0: Associated to a new BSS: BSSID=dc:08:56:13:1e:69
wlan0: Associated with dc:08:56:13:1e:69
wlan0: WPA: Association event - clear replay counter
wlan0: WPA: Clear old PTK
EAPOL: External notification - portEnabled=0
EAPOL: External notification - portValid=0
EAPOL: External notification - EAP success=0
EAPOL: External notification - portEnabled=1
EAPOL: SUPP_PAE entering state CONNECTING
EAPOL: enable timer tick
EAPOL: SUPP_BE entering state IDLE
wlan0: Setting authentication timeout: 10 sec 0 usec
wlan0: Cancelling scan request
wlan0: Cancelling authentication timeout
wlan0: State: ASSOCIATED -> COMPLETED
wlan0: Radio work 'connect'@0x1348f90 done in 0.177806 seconds
wlan0: radio_work_free('connect'@0x1348f90: num_active_works --> 0
wlan0: CTRL-EVENT-CONNECTED - Connection to dc:08:56:13:1e:69 completed [id=0 id_str=]
nl80211: Set wlan0 operstate 0->1 (UP)
netlink: Operstate: ifindex=3 linkmode=-1 (no change), operstate=6 (IF_OPER_UP)
EAPOL: External notification - portValid=1
EAPOL: External notification - EAP success=1
EAPOL: SUPP_PAE entering state AUTHENTICATING
EAPOL: SUPP_BE entering state SUCCESS
EAP: EAP entering state DISABLED
EAPOL: SUPP_PAE entering state AUTHENTICATED
EAPOL: Supplicant port status: Authorized
nl80211: Set supplicant port authorized for dc:08:56:13:1e:69
EAPOL: SUPP_BE entering state IDLE
EAPOL authentication completed - result=SUCCESS
WMM AC: Missing U-APSD configuration
wlan0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
RTM_NEWLINK: ifi_index=3 ifname=wlan0 operstate=6 linkmode=1 ifi_family=0 ifi_flags=0x11043 ([UP][RUNNING][LOWER_UP])
RTM_NEWLINK: ifi_index=3 ifname=wlan0 operstate=6 linkmode=1 ifi_family=0 ifi_flags=0x11043 ([UP][RUNNING][LOWER_UP])
CTRL_IFACE monitor attached /tmp/dhcpcd-pi/libdhcpcd-wpa-623.12\x00
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=3
EAPOL: EAP Session-Id not available
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=169
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=854
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=790
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=806
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=834
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=867
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=647
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=630
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=759
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=484
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=647
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=1085
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=883
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=835
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=912
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=829
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=671
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=981
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=510
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=278
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=0
EAPOL: EAP Session-Id not available
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=169
nl80211: Event message available
nl80211: Drv Event 36 (NL80211_CMD_REG_CHANGE) received for wlan0
nl80211: Regulatory domain change
* initiator=3
* type=0
* alpha2=DE
wlan0: Event CHANNEL_LIST_CHANGED (28) received
wlan0: CTRL-EVENT-REGDOM-CHANGE init=COUNTRY_IE type=COUNTRY alpha2=DE
CTRL-DEBUG: ctrl_sock-sendmsg: sock=12 sndbuf=163840 outq=0 send_len=63
CTRL_IFACE monitor sent successfully to /tmp/dhcpcd-pi/libdhcpcd-wpa-623.12\x00
wlan0: Updating hw mode
nl80211: Regulatory information - country=DE (DFS-ETSI)
nl80211: 2400-2483 @ 40 MHz 20 mBm
nl80211: 5150-5250 @ 80 MHz 20 mBm (no outdoor)
nl80211: 5250-5350 @ 80 MHz 20 mBm (no outdoor) (DFS)
nl80211: 5470-5725 @ 160 MHz 26 mBm (DFS)
nl80211: 5725-5875 @ 80 MHz 13 mBm
nl80211: 57000-66000 @ 2160 MHz 40 mBm
nl80211: Added 802.11b mode based on 802.11g information
EAPOL: startWhen --> 0
EAPOL: disable timer tick
wlan0: Control interface command 'SCAN'
wlan0: Setting scan request: 0.000000 sec
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=3
wlan0: Starting AP scan for wildcard SSID
wlan0: Add radio work 'scan'@0x1348f90
wlan0: First radio work item in the queue - schedule start immediately
wlan0: Starting radio work 'scan'@0x1348f90 after 0.000047 second wait
wlan0: nl80211: scan request
nl80211: Scan SSID - hexdump_ascii(len=0): [NULL]
Scan requested (ret=0) - scan timeout 30 seconds
nl80211: Event message available
nl80211: Drv Event 33 (NL80211_CMD_TRIGGER_SCAN) received for wlan0
wlan0: nl80211: Scan trigger
wlan0: Event SCAN_STARTED (47) received
wlan0: Own scan request started a scan in 0.000200 seconds
CTRL-DEBUG: ctrl_sock-sendmsg: sock=12 sndbuf=163840 outq=0 send_len=24
CTRL_IFACE monitor sent successfully to /tmp/dhcpcd-pi/libdhcpcd-wpa-623.12\x00
RTM_NEWLINK: ifi_index=3 ifname=wlan0 wext ifi_family=0 ifi_flags=0x11043 ([UP][RUNNING][LOWER_UP])
nl80211: Event message available
nl80211: Drv Event 34 (NL80211_CMD_NEW_SCAN_RESULTS) received for wlan0
wlan0: nl80211: New scan results available
nl80211: Scan probed for SSID ''
nl80211: Scan included frequencies: 2412 2417 2422 2427 2432 2437 2442 2447 2452 2457 2462 2467 2472 5180 5200 5220 5240 5260 5280 5300 5320 5500 5520 5540 5560 5580 5600 5620 5640 5660 5680 5700
wlan0: Event SCAN_RESULTS (3) received
wlan0: Scan completed in 3.516924 seconds
nl80211: Associated on 5700 MHz
nl80211: Associated with dc:08:56:13:1e:69
nl80211: Received scan results (18 BSSes)
nl80211: Scan results indicate BSS status with dc:08:56:13:1e:69 as associated
wlan0: BSS: Start scan result update 2
BSS: last_scan_res_used=18/32
wlan0: New scan results available (own=1 ext=0)
CTRL-DEBUG: ctrl_sock-sendmsg: sock=12 sndbuf=163840 outq=0 send_len=24
CTRL_IFACE monitor sent successfully to /tmp/dhcpcd-pi/libdhcpcd-wpa-623.12\x00
wlan0: Radio work 'scan'@0x1348f90 done in 3.523158 seconds
wlan0: radio_work_free('scan'@0x1348f90: num_active_works --> 0
wlan0: Selecting BSS from priority group 0
wlan0: 0: dc:08:56:00:1b:d9 ssid='V11-Home' wpa_ie_len=0 rsn_ie_len=20 caps=0x1511 level=-30 freq=5540
wlan0: skip - SSID mismatch
wlan0: 1: dc:08:56:00:29:19 ssid='V11-Home' wpa_ie_len=0 rsn_ie_len=20 caps=0x1511 level=-49 freq=5300
wlan0: skip - SSID mismatch
wlan0: 2: dc:08:56:00:29:21 ssid='V11-Home' wpa_ie_len=0 rsn_ie_len=20 caps=0x1511 level=-51 freq=5580
wlan0: skip - SSID mismatch
wlan0: 3: dc:08:56:13:1e:69 ssid='ov44b39' wpa_ie_len=0 rsn_ie_len=20 caps=0x511 level=-13 freq=5700
wlan0: selected based on RSN IE
wlan0: selected BSS dc:08:56:13:1e:69 ssid='ov44b39'
RSN: Ignored PMKID candidate without preauth flag
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=854
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=790
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=806
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=834
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=771
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=647
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=630
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=663
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=484
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=647
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=1085
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=883
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=834
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=913
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=828
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=669
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=980
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=510
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=279
CTRL-DEBUG: ctrl_sock-sendto: sock=12 sndbuf=163840 outq=0 send_len=0
Kernel Used
pi@raspberrypi:~/hostap_2_6/wpa_supplicant $ uname -a Linux raspberrypi 4.14.114-v7+ #2 SMP Fri May 17 21:57:57 CEST 2019 armv7l GNU/Linux
Output from Stellar AP (tail -f /tmp/log/wam.log)
1558133238.098527: Custom wireless event: 'Manage.auth 41 freq=5700'
1558133238.098896: freq=5700
1558133238.099159: atheros_raw_receive: subtype 0xb len 41 freq=5700
1558133238.099634: ath11: Event AUTH (10) received
1558133238.099902: New STA
1558133238.100917: ap_sta_add: register ap_handle_timer timeout for b8:27:eb:ea:8c:42 (300 seconds - ap_max_inactivity)
1558133238.102770: _GOLSOH_[ ov44b39 @ ath11 ]: Receive STA <b8:27:eb:ea:8c:42> 80211 Auth event, Auth type OPEN_SYSTEM
1558133238.105133: start get roam flag
1558133238.105403: atheros_sta_auth: addr=b8:27:eb:ea:8c:42 status_code=0
1558133238.115416: Custom wireless event: 'Manage.assoc_req 157 freq=5700'
1558133238.115744: freq=5700
1558133238.115980: atheros_raw_receive: subtype 0x0 len 157 freq=5700
1558133238.117359: ath11: Event ASSOC (0) received
1558133238.118837: _GOLSOH_[ ov44b39 @ ath11 ]: Receive STA <b8:27:eb:ea:8c:42> 80211 assoc event
1558133238.121146: _GOLSOH_[ ov44b39 @ ath11 ]: STA <b8:27:eb:ea:8c:42> included RSN IE in (Re)AssocReq frame
1558133238.122845: [ ov44b39 @ ath11 ]: recv sta assoc frame, reassoc 0
1558133238.123761: RSN IE: STA PMKID - hexdump(len=16): 6d bb 3b a2 09 10 22 9e d9 af 7e 9b 57 65 5f 67
1558133238.126301: _GOLSOH_[ ov44b39 @ ath11 ]: STA <b8:27:eb:ea:8c:42> carried 1 PMKID in RSN IE
1558133238.127505: atheros_sta_assoc: addr=b8:27:eb:ea:8c:42 status_code=0 reassoc 0
1558133238.131594: atheros_del_key: addr=b8:27:eb:ea:8c:42 key_idx=0
1558133238.132067: hostapd_send_trap, send trap ssid ov44b39, type 3
1558133238.132509: wam_send_msg_to_roamtrace, ap mac dc:08:56:13:1e:60
1558133238.133058: wam_send_msg_to_roamtrace, ssid ov44b39
1558133238.133341: wam_send_msg_to_roamtrace, sec 1558133238 , usec 132054, sta sec 1558133238, sta usec 132054
1558133238.133803: wam_send_msg_to_roamtrace,sizeof msg 176, op 3, assoc timestamp 1558133238.132054, auth srv ip 0.0.0.0, auth srv port 0
1558133238.134517: wam_send_msg_to_roamtrace, ap mac dc:08:56:13:1e:60
1558133238.135057: wam_send_msg_to_roamtrace,ssid ov44b39,
1558133238.135334: wam_send_msg_to_roamtrace,authtype 0, iface ath11
1558133238.135644: wam_send_msg_to_roamtrace,encrypto type 3,
1558133238.135920: wam_send_msg_to_roamtrace,sta mac b8:27:eb:ea:8c:42
1558133238.136441: wam_send_msg_to_roamtrace,roamtype 0
1558133238.136700: wam_send_msg_to_roamtrace,user name
1558133238.137097: wam_send_msg_to_roamtrace, sendto succ, msg type 3, sizeofmsg 176
1558133238.137453: IEEE 802.1X: Ignore STA - 802.1X not enabled or forced for WPS
1558133238.137803: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state INITIALIZE
1558133238.138392: atheros_del_key: addr=b8:27:eb:ea:8c:42 key_idx=0
1558133238.138841: atheros_set_sta_authorized: addr=b8:27:eb:ea:8c:42 authorized=0
1558133238.139423: WPA: b8:27:eb:ea:8c:42 WPA_PTK_GROUP entering state IDLE
1558133238.139960: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state AUTHENTICATION
1558133238.140876: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state AUTHENTICATION2
1558133238.142333: WPA: Assign ANonce - hexdump(len=32): 80 7f 37 2e 66 ef 66 66 4c fb 54 33 93 39 3d ac 80 14 ed 55 af 20 59 5e 84 b6 61 2f 9e 3e 75 7a
1558133238.146878: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state INITPSK
1558133238.147518: No PSK for STA trying to use SAE with PMKSA caching
1558133238.147720: SAE: PMK from PMKSA cache
1558133238.147925: No PSK for STA trying to use SAE with PMKSA caching
1558133238.148123: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state PTKSTART
1558133238.148788: RSN: Message 1/4 PMKID from PMKSA entry - hexdump(len=16): 6d bb 3b a2 09 10 22 9e d9 af 7e 9b 57 65 5f 67
1558133238.150007: WPA: Send EAPOL(version=0 secure=0 mic=0 ack=1 install=0 pairwise=1 kde_len=22 keyidx=0 encr=0)
1558133238.150902: WPA: Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 01
1558133238.151945: WPA: Use EAPOL-Key timeout of 1000 ms (retry counter 1)
1558133238.152326: ath11: hostapd_new_assoc_sta: reschedule ap_handle_timer timeout for b8:27:eb:ea:8c:42 (300 seconds - ap_max_inactivity)
1558133238.153447: l2_packet_receive: src=b8:27:eb:ea:8c:42 len=153
1558133238.154149: ath11: Event EAPOL_RX (23) received
1558133238.154400: IEEE 802.1X: 139 bytes from b8:27:eb:ea:8c:42
1558133238.154945: IEEE 802.1X: version=2 type=3 length=135
1558133238.155285: WPA: Received EAPOL-Key from b8:27:eb:ea:8c:42 key_info=0x108 type=2 mic_len=16 key_data_length=40
1558133238.155991: WPA: Received Key Nonce - hexdump(len=32): a2 b6 ea 4f ad 87 49 e2 b0 e9 87 4e c5 8e 16 39 b1 cf c7 3c 39 e3 cf 1f c3 82 e3 ea 70 55 82 af
1558133238.158076: WPA: Received Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 01
1558133238.159174: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state PTKCALCNEGOTIATING
1558133238.159707: WPA: PTK derivation using PRF(SHA256)
1558133238.160429: WPA: PTK derivation - A1=dc:08:56:13:1e:69 A2=b8:27:eb:ea:8c:42
1558133238.161297: WPA: Nonce1 - hexdump(len=32): 80 7f 37 2e 66 ef 66 66 4c fb 54 33 93 39 3d ac 80 14 ed 55 af 20 59 5e 84 b6 61 2f 9e 3e 75 7a
1558133238.163380: WPA: Nonce2 - hexdump(len=32): a2 b6 ea 4f ad 87 49 e2 b0 e9 87 4e c5 8e 16 39 b1 cf c7 3c 39 e3 cf 1f c3 82 e3 ea 70 55 82 af
1558133238.165463: WPA: PMK - hexdump(len=32): [REMOVED]
1558133238.165767: WPA: PTK - hexdump(len=48): [REMOVED]
1558133238.166070: WPA: KCK - hexdump(len=16): [REMOVED]
1558133238.166449: WPA: KEK - hexdump(len=16): [REMOVED]
1558133238.166753: WPA: TK - hexdump(len=16): [REMOVED]
1558133238.167062: WPA: EAPOL-Key MIC using AES-CMAC (AKM-defined - SAE)
1558133238.167433: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state PTKCALCNEGOTIATING2
1558133238.167969: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state PTKINITNEGOTIATING
1558133238.168543: atheros_get_seqnum: addr=00:00:00:00:00:00 idx=1
1558133238.169102: atheros_get_seqnum: addr=00:00:00:00:00:00 idx=4
1558133238.169473: atheros: set80211priv: ath11: ioctl op=0x89f3 (??) len=76 failed: 22 (Invalid argument)
1558133238.170047: atheros_get_seqnum: Failed to get encryption data (addr ff:ff:ff:ff:ff:ff key_idx 4)
1558133238.170774: WPA: Send EAPOL(version=0 secure=1 mic=1 ack=1 install=1 pairwise=1 kde_len=76 keyidx=1 encr=1)
1558133238.171473: WPA: Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 02
1558133238.172385: Plaintext EAPOL-Key Key Data - hexdump(len=88): [REMOVED]
1558133238.172691: WPA: Encrypt Key Data using AES-WRAP (KEK length 16)
1558133238.173277: WPA: EAPOL-Key MIC using AES-CMAC (AKM-defined - SAE)
1558133238.173737: WPA: Use EAPOL-Key timeout of 1000 ms (retry counter 1)
1558133238.175687: l2_packet_receive: src=b8:27:eb:ea:8c:42 len=113
1558133238.176405: ath11: Event EAPOL_RX (23) received
1558133238.176652: IEEE 802.1X: 99 bytes from b8:27:eb:ea:8c:42
1558133238.177203: IEEE 802.1X: version=2 type=3 length=95
1558133238.177544: WPA: Received EAPOL-Key from b8:27:eb:ea:8c:42 key_info=0x308 type=2 mic_len=16 key_data_length=0
1558133238.178251: WPA: Received Key Nonce - hexdump(len=32): 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
1558133238.181199: WPA: Received Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 02
1558133238.182280: WPA: EAPOL-Key MIC using AES-CMAC (AKM-defined - SAE)
1558133238.182630: WPA: b8:27:eb:ea:8c:42 WPA_PTK entering state PTKINITDONE
1558133238.183226: atheros_set_key: alg=3 addr=b8:27:eb:ea:8c:42 key_idx=0
1558133238.185642: ath11: AP-STA-CONNECTED b8:27:eb:ea:8c:42
1558133238.187805: _GOLSOH_[ ov44b39 @ ath11 ]: AP-STA-CONNECTED b8:27:eb:ea:8c:42
1558133238.188736: atheros_set_sta_authorized: addr=b8:27:eb:ea:8c:42 authorized=1
1558133238.190501: ieee802_1x_set_sta_authorized()
1558133238.190755: hostapd_send_trap, send trap ssid ov44b39, type 1
1558133238.191079: wam_send_msg_to_roamtrace, ap mac dc:08:56:13:1e:60
1558133238.191893: wam_send_msg_to_roamtrace, ssid ov44b39
1558133238.192268: wam_send_msg_to_roamtrace, sec 1558133238 , usec 132054, sta sec 1558133238, sta usec 132054
1558133238.192742: wam_send_msg_to_roamtrace,sizeof msg 176, op 1, assoc timestamp 1558133238.132054, auth srv ip 0.0.0.0, auth srv port 0
1558133238.193457: wam_send_msg_to_roamtrace, ap mac dc:08:56:13:1e:60
1558133238.193998: wam_send_msg_to_roamtrace,ssid ov44b39,
1558133238.194344: wam_send_msg_to_roamtrace,authtype 0, iface ath11
1558133238.194658: wam_send_msg_to_roamtrace,encrypto type 3,
1558133238.194937: wam_send_msg_to_roamtrace,sta mac b8:27:eb:ea:8c:42
1558133238.195459: wam_send_msg_to_roamtrace,roamtype 0
1558133238.195719: wam_send_msg_to_roamtrace,user name
1558133238.196146: wam_send_msg_to_roamtrace, sendto succ, msg type 1, sizeofmsg 176
1558133238.196532: wam_authfail_start start
1558133238.196778: wam_ov_author_proc, auth_flag 5, auth_step 5, mac-auth status 1
1558133238.197166: find index 29
1558133238.197399: find arp_node: find name =__ov44b39
1558133238.199412: _GOLSOH_[ ov44b39 @ ath11 ]: Access Role(__ov44b39) from Default (MAC-Auth disable) will be applied to STA <b8:27:eb:ea:8c:42>
1558133238.200564: wam_ov_author_proc :apply_arp.redirect_enable:0, sta->mac_auth_result:1, apply_arp.ExternalCaptivePortal_flag:0,
1558133238.200970: wam_ov_author_proc :sta->cp_auth_success= 0,sta->applied_redirect_url=, sta->roam_flag =0
1558133238.202910: ap_check_some_conditions_value: all conditions isn't satisfied
1558133238.203116: wam_check_send_conditions: all conditions don't match
1558133238.205257: set add macvlan ubus msg: ubus call network.macvlan add_user '{"macAddress":"b8:27:eb:ea:8c:42","vlanID":12}'
1558133238.258041: _GOLSOH_[ ov44b39 @ ath11 ]: Set MAC-vlan, Vlan-ID=[12] for STA <b8:27:eb:ea:8c:42>
1558133238.259020: check policylist .
1558133238.259258: wam_ov_add_policylist, policylist :
1558133238.259758: set policylist ubus msg: ubus call policy set_user_policy '{"macAddress":"b8:27:eb:ea:8c:42","arpName":"__ov44b39","policyListName":"","ifName":"ath11","ssid":"ov44b39","gwMacAddr":"","isolateEnable":0,"wlanSvcName":"ov44b39"}'
1558133238.307074: _GOLSOH_[ ov44b39 @ ath11 ]: Set the PolicyList:[] from Access Role for STA <b8:27:eb:ea:8c:42>
1558133238.307948: wam_ov_ApplyARP : ARP(__ov44b39) applied successful.
1558133238.309842: gateway_mgr ubus msg: ubus call gateway_mgr adduser '{"userMac":"b8:27:eb:ea:8c:42","gwIp":"0.0.0.0"}'
1558133238.353798: hostapd_send_userauthor, send user author notify ssid ov44b39
1558133238.354143: wam_send_msg_to_roamtrace, ap mac dc:08:56:13:1e:60
1558133238.354687: wam_send_msg_to_roamtrace, ssid ov44b39
1558133238.354968: wam_send_msg_to_roamtrace, sec 1558133238 , usec 132054, sta sec 1558133238, sta usec 132054
1558133238.355428: Unknown msg type 18
1558133238.355657: wam_send_msg_to_roamtrace,sizeof msg 176, op 18, assoc timestamp 1558133238.132054, auth srv ip 0.0.0.0, auth srv port 0
1558133238.356363: wam_send_msg_to_roamtrace, ap mac dc:08:56:13:1e:60
1558133238.356905: wam_send_msg_to_roamtrace,ssid ov44b39,
1558133238.357181: wam_send_msg_to_roamtrace,authtype 0, iface ath11
1558133238.357490: wam_send_msg_to_roamtrace,encrypto type 3,
1558133238.357771: wam_send_msg_to_roamtrace,sta mac b8:27:eb:ea:8c:42
1558133238.358288: wam_send_msg_to_roamtrace,roamtype 0
1558133238.358542: wam_send_msg_to_roamtrace,user name
1558133238.358940: wam_send_msg_to_roamtrace, sendto succ, msg type 18, sizeofmsg 176
1558133238.359946: wam send event sta_info_notify, success
1558133238.360377: send_add_user_sync_info enter
1558133238.360969: enter send time 288887--s,220893--us
1558133238.361300: send_ovmode_user_sync_info sta sync size 580
1558133238.361573: send_ovmode_user_sync_info, send cp success 0, mac-au success 0
1558133238.361893: send_ovmode_user_sync_info, append arp name __ov44b39
1558133238.362165: send user sync info dc:08:56:13:1e:69iface ath11,b8:27:eb:ea:8c:42, ssid ov44b39,ipv4 0.0.0.0,userGlobalIPv6 ::, userLocalIPv6 ::, wlan ov44b39, arp __ov44b39
1558133238.368983: sta->sync_type 0, cnt 2
1558133238.369273: sta_add_UserInfoToOtherbss, iface ath11
1558133238.369549: sta_add_UserInfoToOtherbss, find other bss ifname ath01, dc:08:56:13:1e:61, own ifname ath11, dc:08:56:13:1e:69
1558133238.373071: _GOLSOH_[ ov44b39 @ ath01 ]: receive STA <b8:27:eb:ea:8c:42> roaming context, ip 0.0.0.0,userGlobalIPv6 ::, userLocalIPv6 ::, portal Auth success 0, roam flag 0, Sta applied access role __ov44b39, home ap 192.168.10.12
1558133238.373958: find index 29
1558133238.374193: find arp_node: find name =__ov44b39
1558133238.375478: _GOLSOH_save STA <b8:27:eb:ea:8c:42> roaming context in current AP
1558133238.377698: _GOLSOH_[ ov44b39 @ ath11 ]: send SYNC_ADD message to neighbors, STA <b8:27:eb:ea:8c:42> applied access role __ov44b39, sync_type 0, portal Auth fail
1558133238.378579: before nblist time 288887--s,238505--us
1558133238.379067: 1558133238.379216: ath11: STA b8:27:eb:ea:8c:42 WPA: pairwise key handshake completed (RSN)
1558133238.382039: _GOLSOH_[ ov44b39 @ ath11 ]: STA b8:27:eb:ea:8c:42 - pairwise key handshake completed
1558133238.475352: ######handle_dhcp_ipv6....#########
1558133238.874458: ######handle_dhcp....#########
1558133238.876247: _GOLSOH_[ ov44b39 @ ath11 ]: dhcp_snoop: Found DHCPACK for STA b8:27:eb:ea:8c:42 @ IPv4 address 192.168.12.115/24
1558133238.877120: handle_dhcp, don't add sta route,because function return is -1 or -2
1558133238.877331: get_sta_all_ip6addr: ipv6_num = 0
1558133238.877745: send message to track successful
1558133238.878010: handle_dhcp, (2)sta->sta_gateway = 192.168.12.254
1558133238.878410: gateway_mgr ubus msg: ubus call gateway_mgr adduser '{"userMac":"b8:27:eb:ea:8c:42","gwIp":"192.168.12.254"}'
1558133238.925232: send_add_user_sync_info enter
1558133238.925579: enter send time 288887--s,785502--us
1558133238.925915: send_ovmode_user_sync_info sta sync size 580
1558133238.926239: send_ovmode_user_sync_info, send cp success 0, mac-au success 0
1558133238.926684: send_ovmode_user_sync_info, append arp name __ov44b39
1558133238.927013: send user sync info dc:08:56:13:1e:69iface ath11,b8:27:eb:ea:8c:42, ssid ov44b39,ipv4 192.168.12.115,userGlobalIPv6 ::, userLocalIPv6 ::, wlan ov44b39, arp __ov44b39
1558133238.930578: sta->sync_type 0, cnt 2
1558133238.930946: sta_add_UserInfoToOtherbss, iface ath11
1558133238.931295: sta_add_UserInfoToOtherbss, find other bss ifname ath01, dc:08:56:13:1e:61, own ifname ath11, dc:08:56:13:1e:69
1558133238.935488: _GOLSOH_[ ov44b39 @ ath01 ]: receive STA <b8:27:eb:ea:8c:42> roaming context, ip 192.168.12.115,userGlobalIPv6 ::, userLocalIPv6 ::, portal Auth success 0, roam flag 0, Sta applied access role __ov44b39, home ap 192.168.10.12
1558133238.936418: find index 29
1558133238.936652: find arp_node: find name =__ov44b39
1558133238.938383: _GOLSOH_delete STA <b8:27:eb:ea:8c:42> roaming context in current AP
1558133238.941032: _GOLSOH_save STA <b8:27:eb:ea:8c:42> roaming context in current AP
1558133238.943818: _GOLSOH_[ ov44b39 @ ath11 ]: send SYNC_ADD message to neighbors, STA <b8:27:eb:ea:8c:42> applied access role __ov44b39, sync_type 0, portal Auth fail
1558133238.945354: before nblist time 288887--s,805277--us
1558133238.946090: ######handle_dhcp....#########
1558133238.946656: ######handle_dhcp....#########
1558133238.947198: ######handle_dhcp....#########
1558133239.170348: send message to adme successful, operation = 1, megtype = 1
1558133239.504466: ######handle_dhcp_ipv6....#########
1558133239.505199: _GOLSOH_[ ov44b39 @ ath11 ]: handle_dhcpv6_icmpv6: Found DHCPv6 ACK for STA b8:27:eb:ea:8c:42 @ IPv6 address fe80::13de:b443:e411:7bc7
1558133239.505657: handle_dhcpv6_icmpv6, don't add sta route,because function return is -1 or -2
1558133239.505785: get_sta_all_ip6addr: IPv6 address fe80::13de:b443:e411:7bc7
1558133239.505899: get_sta_all_ip6addr: ipv6_num = 1
1558133239.506185: send message to track successful
1558133239.506333: get_sta_global_or_local_ip6addr: get IPv6 local-address for b8:27:eb:ea:8c:42
1558133239.510433: wam send event sta_info_notify, success
1558133239.510575: send_add_user_sync_info enter
1558133239.510681: enter send time 288888--s,370614--us
1558133239.510815: send_ovmode_user_sync_info sta sync size 580
1558133239.510926: send_ovmode_user_sync_info, send cp success 0, mac-au success 0
1558133239.511055: get_sta_global_or_local_ip6addr: get IPv6 local-address for b8:27:eb:ea:8c:42
1558133239.511272: send_ovmode_user_sync_info, append arp name __ov44b39
1558133239.511403: send user sync info dc:08:56:13:1e:69iface ath11,b8:27:eb:ea:8c:42, ssid ov44b39,ipv4 192.168.12.115,userGlobalIPv6 ::, userLocalIPv6 fe80::13de:b443:e411:7bc7, wlan ov44b39, arp __ov44b39
1558133239.512712: sta->sync_type 0, cnt 2
1558133239.512833: sta_add_UserInfoToOtherbss, iface ath11
1558133239.512945: sta_add_UserInfoToOtherbss, find other bss ifname ath01, dc:08:56:13:1e:61, own ifname ath11, dc:08:56:13:1e:69
1558133239.514262: _GOLSOH_[ ov44b39 @ ath01 ]: receive STA <b8:27:eb:ea:8c:42> roaming context, ip 192.168.12.115,userGlobalIPv6 ::, userLocalIPv6 ::, portal Auth success 0, roam flag 0, Sta applied access role __ov44b39, home ap 192.168.10.12
1558133239.514627: find index 29
1558133239.514721: find arp_node: find name =__ov44b39
1558133239.515244: _GOLSOH_delete STA <b8:27:eb:ea:8c:42> roaming context in current AP
1558133239.516041: _GOLSOH_save STA <b8:27:eb:ea:8c:42> roaming context in current AP
1558133239.516957: _GOLSOH_[ ov44b39 @ ath11 ]: send SYNC_ADD message to neighbors, STA <b8:27:eb:ea:8c:42> applied access role __ov44b39, sync_type 0, portal Auth fail
1558133239.517315: before nblist time 288888--s,377247--us
1558133241.059063: Global ctrl_iface command: STA_LIST
TODO
- Describe how to build custom kernel
- Describe how to embed firmware blob
- Describe how to get custom wpa_supplicant
stellar-wireless-wpa3-sae-raspberry-pi.1558135022.txt.gz · Zuletzt geändert: (Externe Bearbeitung)